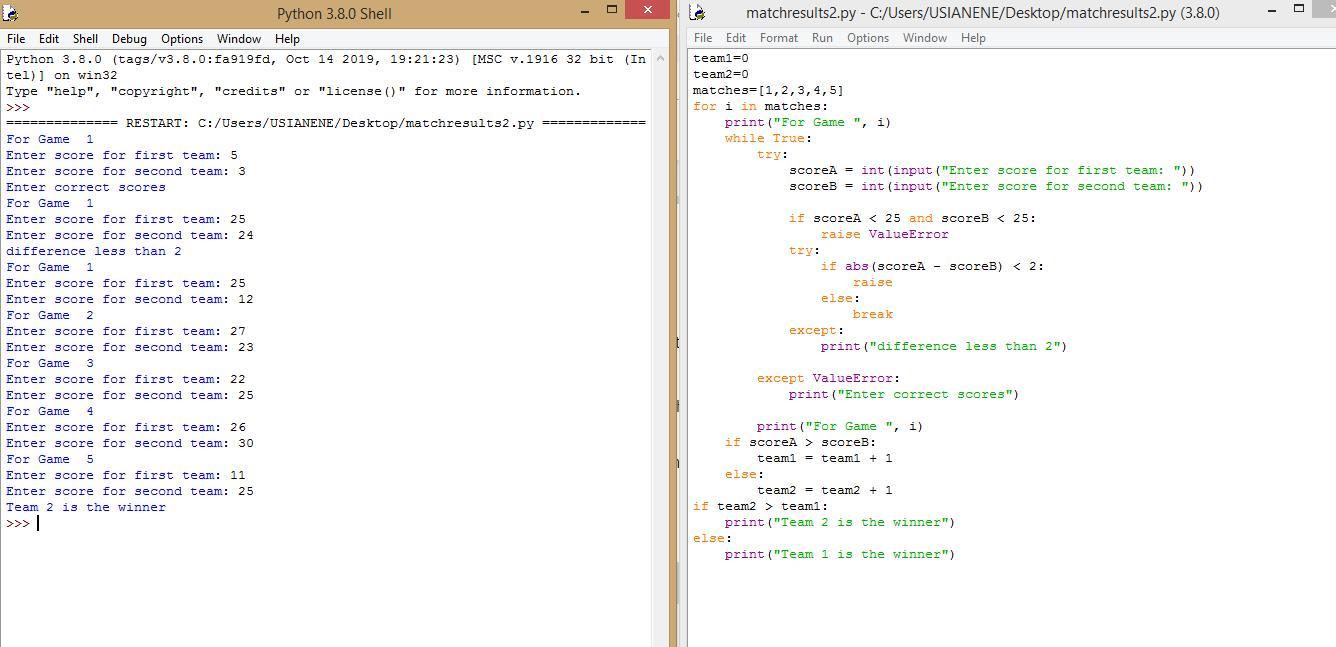
Answer:
#section 1
team1=0
team2=0
matches=[1,2,3,4,5]
for i in matches:
print("For Game ", i)
#section 2
while True:
try:
scoreA = int(input("Enter score for first team: "))
scoreB = int(input("Enter score for second team: "))
if scoreA < 25 and scoreB < 25:
raise ValueError
try:
if abs(scoreA - scoreB) < 2:
raise
else:
break
except:
print("difference less than 2")
except ValueError:
print("Enter correct scores")
#section 3
print("For Game ", i)
if scoreA > scoreB:
team1 = team1 + 1
else:
team2 = team2 + 1
#section 4
if team2 > team1:
print("Team 2 is the winner")
else:
print("Team 1 is the winner")
Explanation:
There is no way you can run the code without using a break statement because, in a while loop you have to pass an argument that will exit the loop. if you don't your loop will keep running and that's not good.
You might have also gone about it in a way that is a bit complicated. when writing code always look out for ways to make your work easier.
I used a For Loop, While Loop and an array.
#section 1
team1=0
team2=0
matches=[1,2,3,4,5]
for i in matches:
print("For Game ", i)
- In this section two variables were declared two variables to hold the final results after both teams have played their 5 games and their scores recorded
- An Array holding the number of games they're to play was also declared. they are playing 5 so the Array "matches" holds 5 elements.
- The first loop here is the "For loop" and what it does is to run the block of code under it for all the elements in the Array.
- finally we print for game "i" where i is each game in the array
#section 2
while True:
try:
scoreA = int(input("Enter score for first team: "))
scoreB = int(input("Enter score for second team: "))
if scoreA < 25 and scoreB < 25:
raise ValueError
try:
if abs(scoreA - scoreB) < 2:
raise
else:
break
except:
print("difference less than 2")
except ValueError:
print("Enter correct scores")
- A while loop is always true unless it encounters an argument that is not true or a break statement is inserted.
- This section is responsible for taking all the inputs required and if a wrong input is entered it would show the specific error and ask you to make the input again.
- Here the Try and Except is use to handle the errors. When the Try block encounters an error it goes to the Except block and executes whatever it finds there.
- The first try block prompts and takes inputs, it then checks if the values inputted satisfies or violates the 25-point rule.
If it does not satisfy the 25-point rule, it goes to it's error block and prints "enter correct score" and the WHILE loop runs again.
within this Try block is nested another try block. if the first try block does not raise any error it proceeds to the second try block.
- The second Try block checks the difference between the scores and if it is less than 2, it raises an error and prints difference is less than 2 and runs the WHILE loop again.
- If there are no errors it BREAKS out of the WHILE loop then the FOR loop moves to the next match.
#section 3
print("For Game ", i)
if scoreA > scoreB:
team1 = team1 + 1
else:
team2 = team2 + 1
- Remember there is still a for loop. This section prints the game we just recorded, and checks which team won. It then adds the win as a point(1) to the teams total score.
#section 4
if team2 > team1:
print("Team 2 is the winner")
else:
print("Team 1 is the winner")
- In this section the For Loop has finished running and the final values are ready, it compares the scores of both teams and declares the winner.
I have placed an attachment to help you see the code in action.