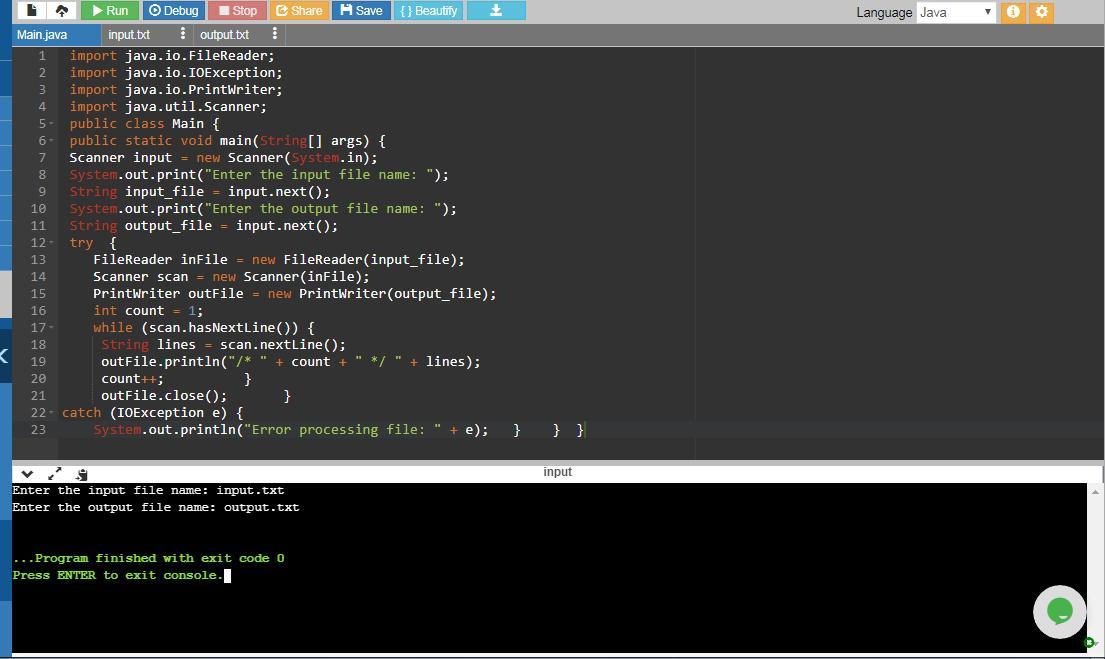
Answer:
I am writing a JAVA program:
import java.io.FileReader; // class used for reading data from a file
import java.io.IOException; //class used for handling exceptions
import java.io.PrintWriter; // class used to printing or writing formatted data. It is used when the data to be written contains text and numbers
import java.util.Scanner; // class used to take input from the user
public class Main { //start of the class
public static void main(String[] args) {//start of main() function body
Scanner input = new Scanner(System.in); //creates Scanner class object
System.out.print("Enter the input file name: "); // prompts user to enter the input file name
String input_file = input.next(); //to read and return the token i.e. input file name and store this into input_file String type variable
System.out.print("Enter the output file name: "); // prompts user to enter the output file name
String output_file = input.next(); /to read and return the token i.e. output file name and store this into output_file String type variable
try {/* try defines a chunk of code to be tested for errors during the execute of this chunk. its a code block for reading from input file and writing to output file. This handles the exception if program cannot create or write to the file indicated. */
FileReader inFile = new FileReader(input_file); //creates object inFile of FileReader class to read the input_file contents
Scanner scan = new Scanner(inFile); //read and scans the input file
PrintWriter outFile = new PrintWriter(output_file); //creates object outFile of PrintWriter class to write to the output file. It is used to write output data in a readable text form.
int count = 1; //counts the line number
while (scan.hasNextLine()) { //loop keeps checking for the next line in input file
String lines = scan.nextLine(); // reads the entire line of the input file and stores that line contents in String lines
outFile.println("/* " + count + " */ " + lines); //each line represented with line number enclosed in /* */
count++; } //increments the line number at each iteration
outFile.close(); } //closes the output file after writing the contents from input file with each line of the input file enclosed in /* */
catch (IOException e) { // catching the IOException and prints the following message if program cannot create input_file or write to the output_file
System.out.println("Error processing file: " + e); } } }
Explanation:
The program is well explained in the comments mentioned with each statement of the above program. The user is prompted to enter input and output file names. Then the program uses a while loop that scans through lines of the input file and count variable counts each line of input file. Then at each iteration the count variable counts a line of input file and line number of each line of the input file is enclosed in /* */ delimiters. The contents of input file, in which the line numbers of text lines of the input file are enclosed in /* */ delimiters, is written to the output file.
The screenshot of the program is attached along with the output file produces as a result of this program execution.