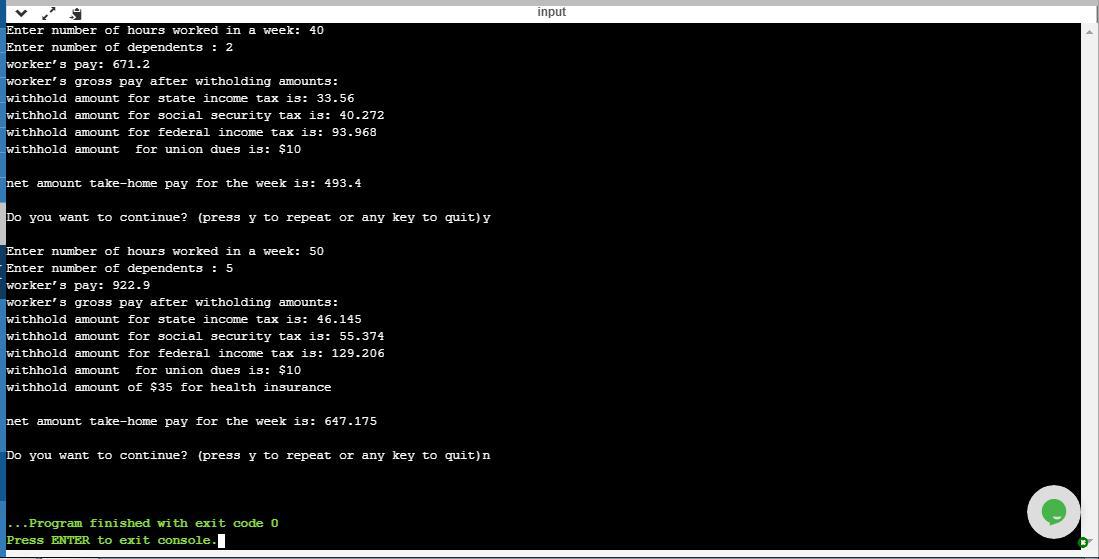
Answer:
Here is the C++ program:
#include<iostream> // to use input output functions
using namespace std; //to access objects cin cout
int main() { //start of main function
int hrsWorked; //stores the number of hours worked
int dependents; //stores the number of dependents
double grossPay; //stores the gross pay
char choice; //store the value for choice of user to continue
do { //loop that keeps repeating as often as the user wishes
cout<<"Enter number of hours worked in a week: "; // prompts user to enter number of weeks
cin>>hrsWorked; //reads input value for number of hours worked
cout<<"Enter number of dependents : "; // prompts user to enter number of dependents
cin>>dependents; //reads input value for number of dependents
if(hrsWorked>40) //if hours worked are more than 40
{grossPay = ((40 * 16.78) + (hrsWorked-40)*(16.78*1.5)); } //employee is paid at the overtime rate of one and-one-half times
else //if hours worked are not more than 40
{ grossPay = (hrsWorked*16.78);} // employee is paid at a rate of $16.78 per hour
double ssTax = 0.06* grossPay ; //computes 6% Social Security tax withheld from gross pay
double fIncomeTax = 0.14* grossPay; //computes 14% federal income tax withheld from gross pay
double sIncomeTax = 0.05 * grossPay; //computes 5% state income tax withheld from gross pay
cout<<"worker’s pay: "<<grossPay<<endl; //displays workers pay
cout<<"worker’s gross pay after withholding amounts:"<<endl; //displays workers pay including withholding amounts
cout<<"withhold amount for state income tax is: "<<sIncomeTax<<endl; //displays grosspay with state income tax withheld
cout<<"withhold amount for social security tax is: "<<ssTax<<endl; //displays grosspay with Social Security tax withheld
cout<<"withhold amount for federal income tax is: "<<fIncomeTax<<endl; //displays grosspay with federeal income tax withheld
cout<<"withhold amount for union dues is: $10 "<<endl; // $10 per week is withheld for union dues
if(dependents >= 3) { //if worker has three or more dependents
cout<<"withhold amount of $35 for health insurance "<<endl;
grossPay = grossPay - 35; } //an additional $35 is withheld to cover the extra cost of health insurance beyond what the employer pays
cout<<endl; //prints a new line
double take_homepay; //stores the net take-home pay for the week.
take_homepay = ((grossPay- ssTax- sIncomeTax - fIncomeTax) - 10); //compute the net t ake-home pay for the week
cout<<"net amount take-home pay for the week is: "<<take_homepay; //displays the net take-home pay for the week
cout<<endl; //prints a new line
cout<<"\nDo you want to continue? (press y to repeat or any key to quit)"; //ask user to repeat the calculation
cin>>choice; //reads choice from user
cout<<endl; //prints a new line
}while(choice =='y' || choice =='Y'); } //loop continues to execute till user wants to repeat calculations and stops when user presses any key other than y or Y
Explanation:
The program works as follows:
Suppose number of working hours is 40 and number of dependents is 2
hrsWorked = 40
dependents = 2
if(hrsWorked>40) this condition evaluates to false because hrsWorked is equal to 40 so else part executes:
grossPay = (hrsWorked*16.78); this becomes:
grossPay = 40 * 16.78
grossPay = 671.2
double ssTax = 0.06* grossPay ; this statement withholds 6% Social Security tax from gross pay. This becomes:
ssTax = 0.06* 671.2;
ssTax = 40.272
double fIncomeTax = 0.14* grossPay; this statement withholds 14% federal income tax from gross pay. This becomes:
fIncomeTax = 0.14* 671.2;
fIncomeTax = 93.968
double sIncomeTax = 0.05 * grossPay; this statement withholds 5% state income tax from gross pay. This becomes:
sIncomeTax = 0.05 * 671.2
sIncomeTax = 33.56
if(dependents >= 3) this condition is false because number of dependents is 2
Next to compute net take-home pay the program control moves to the statement:
take_homepay = ((grossPay- ssTax- sIncomeTax - fIncomeTax) - 10)
this becomes:
take_homepay = ((671.2 - 40.272 - 33.56 - 93.968) - 10)
Note that the 10 here is the $10 per week which is withheld for union dues.
take_homepay = ((671.2 - 40.272 - 33.56 - 93.968) - 10)
take_homepay = 503.4 - 10
take_homepay = 493.4
The screenshot of the output of this program is attached.