Answer:
1)
for(i = 0; i < NUM_VALS; ++i) {
if(userValues[i] == matchValue) {
numMatches++; } }
2)
for (i = 0; i < NUM_GUESSES; i++) {
scanf("%d", &userGuesses[i]); }
for (i = 0; i < NUM_GUESSES; ++i) {
printf("%d ", userGuesses[i]); }
3)
sumExtra = 0;
for (i = 0; i < NUM_VALS; ++i){
if (testGrades[i] > 100){
sumExtra = testGrades[i] - 100 + sumExtra; } }
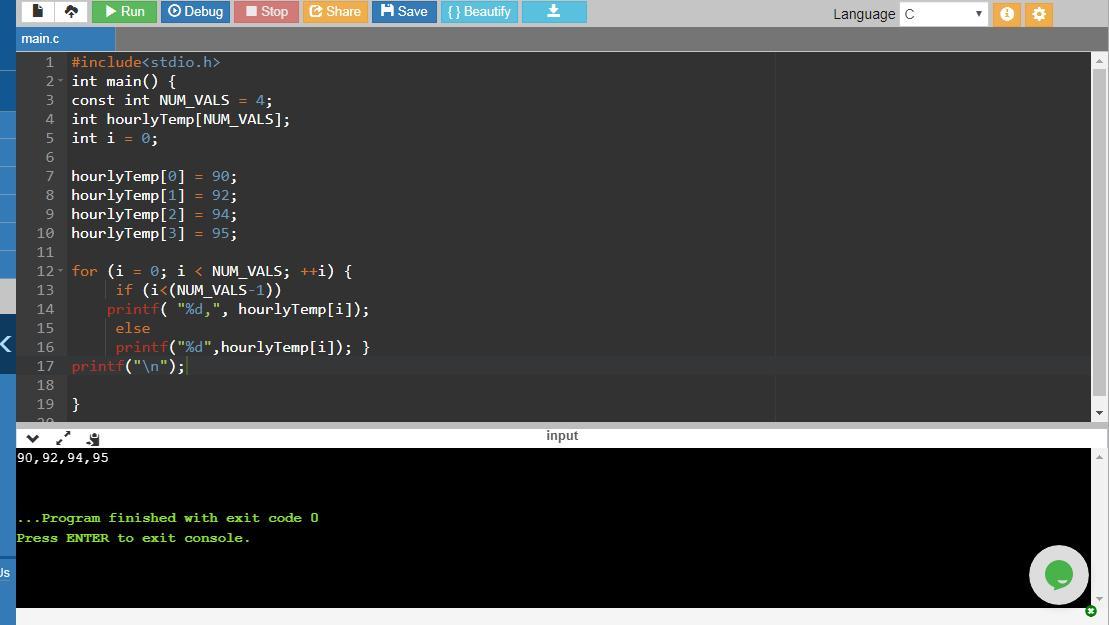
4)
for (i = 0; i < NUM_VALS; ++i) {
if (i<(NUM_VALS-1))
printf( "%d,", hourlyTemp[i]);
else
printf("%d",hourlyTemp[i]); }
Explanation:
1) This loop works as follows:
1st iteration:
i = 0
As i= 0 and NUM_VALS = 4 This means for condition i<NUM_VALS is true so the body of loop executes
if(userValues[i] == matchValue) condition checks if element at i-th index position of userValues[] array is equal to the value of matchValue variable. As matchValue = 2 and i = 0 So the statement becomes:
userValues[0] == 2
2 == 2
As the value at 0th index (1st element) of userValues is 2 so the above condition is true and the value of numMatches is incremented to 1. So numMatches = 1
Now value of i is incremented to 1 so i=1
2nd iteration:
i = 1
As i= 1 and NUM_VALS = 4 This means for condition i<NUM_VALS is true so the body of loop executes
if(userValues[i] == matchValue) condition checks if element at i-th index position of userValues[] array is equal to the value of matchValue variable. As matchValue = 2 and i = 1 So the statement becomes:
userValues[1] == 2
2 == 2
As the value at 1st index (2nd element) of userValues is 2 so the above condition is true and the value of numMatches is incremented to 1. So numMatches = 2
Now value of i is incremented to 1 so i=2
The same procedure continues at each iteration.
The last iteration is shown below:
5th iteration:
i = 4
As i= 4 and NUM_VALS = 4 This means for condition i<NUM_VALS is false so the loop breaks
Next the statement: printf("matchValue: %d, numMatches: %d\n", matchValue, numMatches); executes which displays the value of
numMatches = 3
2)
The first loop works as follows:
At first iteration:
i = 0
i<NUM_GUESSES is true as NUM_GUESSES = 3 and i= 0 so 0<3
So the body of loop executes which reads the element at ith index (0-th) index i.e. 1st element of userGuesses array. Then value of i is incremented to i and i = 1.
At each iteration each element at i-th index is read using scanf such as element at userGuesses[0], userGuesses[1], userGuesses[2]. The loop stops at i=4 as i<NUM_GUESSES evaluates to false.
The second loop works as follows:
At first iteration:
i = 0
i<NUM_GUESSES is true as NUM_GUESSES = 3 and i= 0 so 0<3
So the body of loop executes which prints the element at ith index (0-th) index i.e. 1st element of userGuesses array. Then value of i is incremented to i and i = 1.
At each iteration, each element at i-th index is printed on output screen using printf such as element at userGuesses[0], userGuesses[1], userGuesses[2] is displayed. The loop stops at i=4 as i<NUM_GUESSES evaluates to false.
So if user enters enters 9 5 2, then the output is 9 5 2
3)
The loop works as follows:
At first iteration:
i=0
i<NUM_VALS is true as NUM_VALS = 4 so 0<4. Hence the loop body executes.
if (testGrades[i] > 100 checks if the element at i-th index of testGrades array is greater than 100. As i=0 so this statement becomes:
if (testGrades[0] > 100
As testGrades[0] = 101 so this condition evaluates to true as 101>100
So the statement sumExtra = testGrades[i] - 100 + sumExtra; executes which becomes:
sumExtra = testGrades[0] - 100 + sumExtra
As sumExtra = 0
testGrades[0] = 101
So
sumExtra = 101 - 100 + 0
sumExtra = 1
The same procedure is done at each iteration until the loop breaks. The output is:
sumExtra = 8
4)
The loop works as follows:
At first iteration
i=0
i < NUM_VALS is true as NUM_VALS = 4 so 0<4 Hence loop body executes.
if (i<(NUM_VALS-1)) checks if i is less than NUM_VALS-1 which is 4-1=3
It is also true as 0<3 Hence the statement in body of i executes
printf( "%d,", hourlyTemp[i]) statement prints the element at i-th index i.e. at 0-th index of hourlyTemp array with a comma (,) in the end. As hourlyTemp[0] = 90; So 90, is printed.
When the above IF condition evaluates to false i.e. when i = 3 then else part executes which prints the hourlyTemp[3] = 95 without comma.
Same procedure happens at each iteration unless value of i exceeds NUM_VAL.
The output is:
90, 92, 94, 95
The programs along with their output are attached.