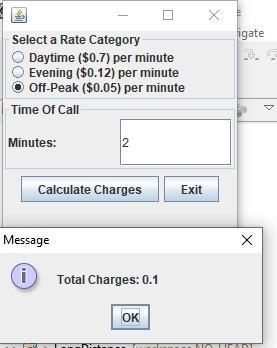
Answer:
Kindly note that, you're to replace "at" with shift 2 as the brainly text editor can't take the symbol
Explanation:
Below is the Java Swing implementation of the assignment.
=========================== LongDistance.java ====================================
import java.awt.GridLayout;
import javax.swing.*;
public class LongDistance extends JFrame{
/**
*
*/
public static float rate;
public static float minutes;
public static float total;
LongDistance(){
RatePanel rp = new RatePanel();
MinutesPanel mp = new MinutesPanel();
ButtonsPanel bp = new ButtonsPanel();
this.setLayout(new GridLayout(3, 1));
this.add(rp);
this.add(mp);
this.add(bp);
this.setDefaultCloseOperation(EXIT_ON_CLOSE);
this.setSize(250, 250);
this.setVisible(true);
}
}
============================ RatePanel.java ==================================
import java.awt.Dimension;
import java.awt.GridLayout;
import java.awt.event.ActionEvent;
import java.awt.event.ActionListener;
import javax.swing.BorderFactory;
import javax.swing.ButtonGroup;
import javax.swing.JPanel;
import javax.swing.JRadioButton;
import javax.swing.border.Border;
public class RatePanel extends JPanel implements ActionListener {
/**
*
*/
private JRadioButton jr1, jr2, jr3;
RatePanel(){
Border panelBorder = BorderFactory.createTitledBorder("Select a Rate Category");
jr1 = new JRadioButton("Daytime ($0.7) per minute");
jr2 = new JRadioButton("Evening ($0.12) per minute");
jr3 = new JRadioButton("Off-Peak ($0.05) per minute");
ButtonGroup bg = new ButtonGroup();
this.setLayout(new GridLayout(3,1));
this.setBorder(panelBorder);
this.setPreferredSize(new Dimension(800, 150));
this.add(jr1);
this.add(jr2);
this.add(jr3);
bg.add(jr1);
bg.add(jr2);
bg.add(jr3);
jr1.addActionListener(this);
jr2.addActionListener(this);
jr3.addActionListener(this);
}
"at"Override
public void actionPerformed(ActionEvent arg0) {
// TODO Auto-generated method stub
if(arg0.getSource() == jr1){
LongDistance.rate = 0.07f;
}
if(arg0.getSource() == jr2){
LongDistance.rate = 0.12f;
}
if(arg0.getSource() == jr3){
LongDistance.rate = 0.05f;
}
}
}
=============================== MinutesPanel.java =============================
import java.awt.Dimension;
import java.awt.GridLayout;
import java.awt.event.ActionEvent;
import java.awt.event.ActionListener;
import java.awt.event.KeyEvent;
import java.awt.event.KeyListener;
import javax.swing.*;
import javax.swing.border.Border;
import javax.swing.event.DocumentListener;
public class MinutesPanel extends JPanel implements KeyListener{
JTextField jt;
MinutesPanel(){
Border panelBorder = BorderFactory.createTitledBorder("Time Of Call");
this.setLayout(new GridLayout(1, 2));
JLabel jl = new JLabel("Minutes: ");
jt = new JTextField();
jt.setBounds(50,50,150,20);
this.setPreferredSize(new Dimension(10, 10));
this.setBorder(panelBorder);
this.add(jl);
this.add(jt);
jt.addKeyListener(this);
}
"at"Override
public void keyPressed(KeyEvent arg0) {
// TODO Auto-generated method stub
}
"at"Override
public void keyReleased(KeyEvent arg0) {
// TODO Auto-generated method stub
if(jt.getText() != "")
LongDistance.minutes = Float.parseFloat(jt.getText());
}
"at"Override
public void keyTyped(KeyEvent arg0) {
// TODO Auto-generated method stub
}
}
============================= ButtonsPanel.java ============================
import java.awt.event.ActionEvent;
import java.awt.event.ActionListener;
import javax.swing.JButton;
import javax.swing.JOptionPane;
import javax.swing.JPanel;
public class ButtonsPanel extends JPanel implements ActionListener{
JButton calculate;
JButton exit;
ButtonsPanel(){
calculate = new JButton("Calculate Charges");
exit = new JButton("Exit");
this.add(calculate);
this.add(exit);
calculate.addActionListener(this);
exit.addActionListener(this);
}
"at"Override
public void actionPerformed(ActionEvent arg0) {
// TODO Auto-generated method stub
if(arg0.getSource() == calculate){
System.out.println("r " + LongDistance.rate);
System.out.println("m " + LongDistance.minutes);
LongDistance.total = LongDistance.rate * LongDistance.minutes;
JOptionPane.showMessageDialog(null, "Total Charges: " +LongDistance.total);
}
if(arg0.getSource() == exit){
System.exit(0);
}
}
}
============================ App.java==============================
public class App {
public static void main(String[] args) {
LongDistance ld = new LongDistance();
}
}
Check the output below