Answer:
Here is the C++ program for Employee class with fields id,name and sal.
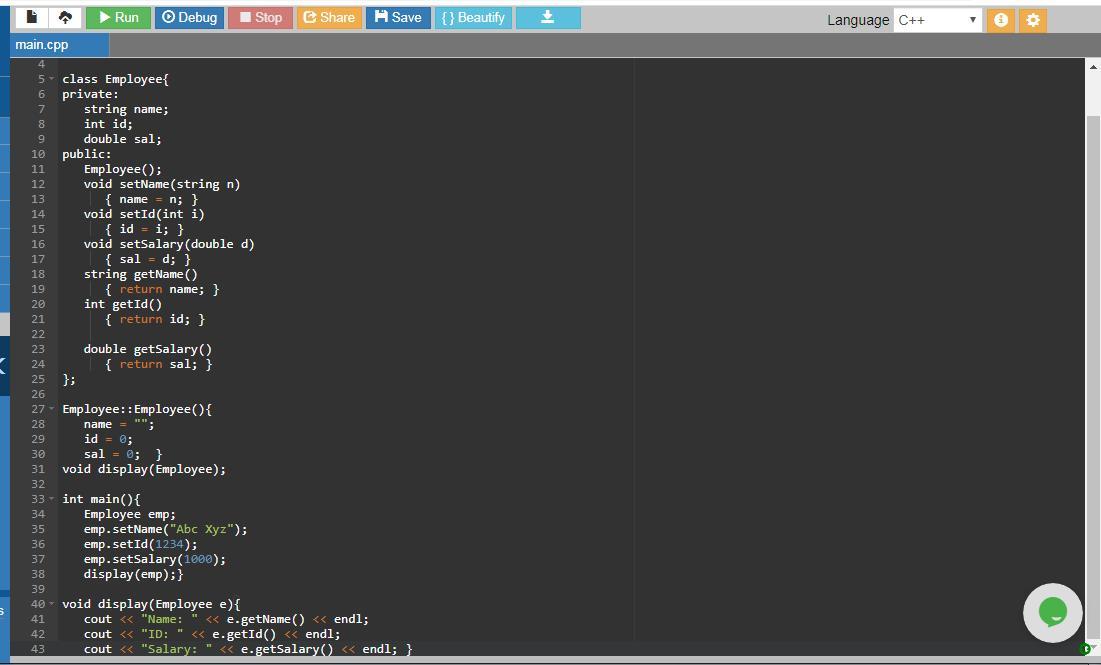
#include <iostream> // to use input output functions
#include <string> //to manipulate and use strings
using namespace std; // to access objects like cin cout
class Employee { //class Employee
private:
/* the following data members are declared as private which means they can only be accessed by the functions within Employee class */
string name; //name field
int id; //id field
double sal; //salary field
public:
Employee(); // constructor that initializes an object when it is created
/* setName, setID and setSalary are the mutators which are the methods used to change data members. This means they set the values of a private fields i.e. name, id and sal */
void setName(string n) //mutator for name field
{ name = n; }
void setId(int i) //mutator for id field
{ id = i; }
void setSalary(double d) //mutator for sal field
{ sal = d; }
/* getName, getID and getSalary are the accessors which are the methods used to read data members. This means they get or access the values of a private fields i.e. name, id and sal */
string getName() //accessor for name field
{ return name; }
int getId() //accessor for id field
{ return id; }
double getSalary() //accessor for sal field
{ return sal; } };
Employee::Employee() { //default constructor where the fields are initialized
name = ""; // name field initialized
id = 0; // id field initialized to 0
sal = 0; } // sal field initialized to 0
void display(Employee);
// prototype of the method display() to display the data of Employee
int main() { //start of the main() function body
Employee emp; //creates an object emp of Employee class
/*set the name field to Abc Xyz which means set the value of Employee class name field to Abc Xyz through setName() method and object emp */
emp.setName("Abc Xyz");
/*set the id field to 1234 which means set the value of Employee class id field to 1234 through setId() method and object emp */
emp.setId(1234);
/*set the sal field to 1000 which means set the value of Employee class sal field to 1000 through setSalary() method and object emp */
emp.setSalary(1000);
display(emp); } //calls display() method to display the Employee data
void display(Employee e) { // this method displays the data in the Employee //class object passed as a parameter.
/*displays the name of the Employee . This name is read or accessed through accessor method getName() and object e of Employee class */
cout << "Name: " << e.getName() << endl;
/*displays the id of the Employee . This id is read or accessed by accessor method getId() and object e */
cout << "ID: " << e.getId() << endl;
/*displays the salary of the Employee . This sal field is read or accessed by accessor method getSalary() and object e */
cout << "Salary: " << e.getSalary() << endl; }
Explanation:
The program is well explained in the comments mentioned with each statement of the program.
The program has a class Employee which has private data members id, name and sal, a simple default constructor Employee(), mutatator methods setName, setId and setSalary to set the fields, acccessor method getName, getId and getSalary to get the fields values.
A function display( ) is used to display the Employee data i.e. name id and salary of Employee.
main() has an object emp of Employee class in order to use data fields and access functions defined in Employee class.
The output of the program is:
Name: Abc Xyz
ID: 1234
Salary: 1000
The program and its output are attached.