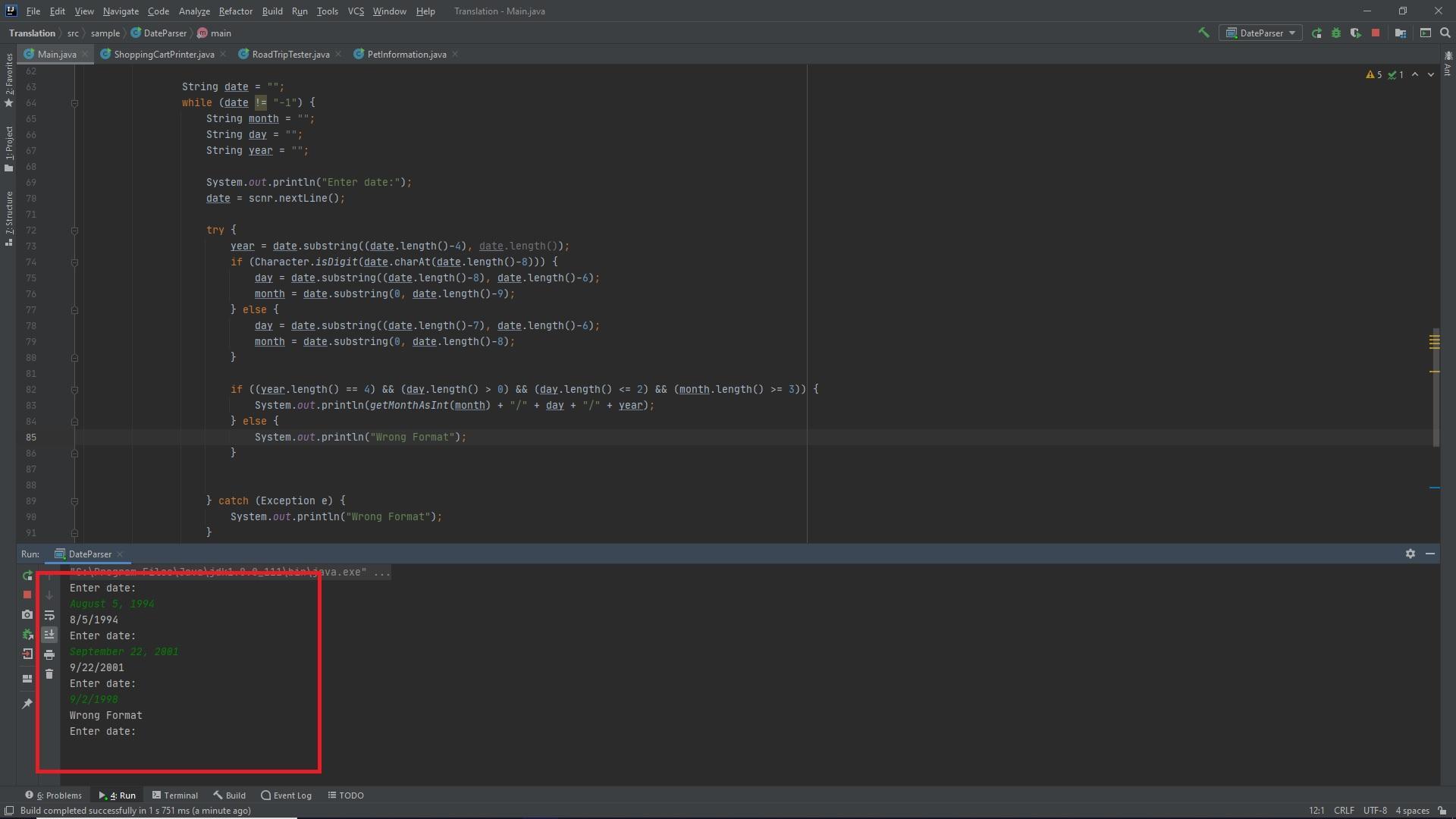
Answer:
Explanation:
The following is the entire modified code, it takes in the date as an input and continues changing the dates to the desired format. If the input format is wrong it says "Wrong Format" and requests another input. If -1 is passed as an input the program terminates.
import java.util.Scanner;
class DateParser {
public static int getMonthAsInt(String monthString) {
int monthInt;
switch (monthString) {
case "January" :
monthInt = 1;
break;
case "February":
monthInt = 2;
break;
case "March":
monthInt = 3;
break;
case "April":
monthInt = 4;
break;
case "May":
monthInt = 5;
break;
case "June":
monthInt = 6;
break;
case "July":
monthInt = 7;
break;
case "August":
monthInt = 8;
break;
case "September":
monthInt = 9;
break;
case "October":
monthInt = 10;
break;
case "November":
monthInt = 11;
break;
case "December":
monthInt = 12;
break;
default:
monthInt = 0;
}
return monthInt;
}
public static void main(String[] args) {
Scanner scnr = new Scanner(System.in);
// TODO: Read dates from input, parse the dates to find the one
// in the correct format, and output in m/d/yyyy format
String date = "";
while (!date.equals("-1")) {
String month = "";
String day = "";
String year = "";
System.out.println("Enter date:");
date = scnr.nextLine();
try {
year = date.substring((date.length()-4), date.length());
if (Character.isDigit(date.charAt(date.length()-8))) {
day = date.substring((date.length()-8), date.length()-6);
month = date.substring(0, date.length()-9);
} else {
day = date.substring((date.length()-7), date.length()-6);
month = date.substring(0, date.length()-8);
}
if ((year.length() == 4) && (day.length() > 0) && (day.length() <= 2) && (month.length() >= 3)) {
System.out.println(getMonthAsInt(month) + "/" + day + "/" + year);
} else {
System.out.println("Wrong Format");
}
} catch (Exception e) {
System.out.println("Wrong Format");
}
}
}
}