Answer:
Here is the JAVA program :
import javax.swing.JOptionPane; //to use JOptionPane
public class Main { //class name
public static void main(String[] args) { //start of main method
int ECount= 0; //counts number of upper case E
int eCount= 0; //counts number of lower case e
String sentence; //stores input sentence string
sentence = JOptionPane.showInputDialog(null, "Type a sentence (type stop to exit)"); //uses showInputDialog method to display a dialog box which prompts user to enter a sentence
int length = sentence.length(); //stores the length of the sentence
while (!sentence.equalsIgnoreCase("stop")) //the loop continues to execute until the user types stop
{ for (int i = 0; i < length; i++) { //loops through the sentence
if (sentence.charAt(i) == 'E') //if the character is an uppercase E
ECount += 1; //adds 1 to the count of Ecount
if (sentence.charAt(i) == 'e') //if the character in a sentence is lowercase e
eCount += 1;} //adds 1 to the count of lower case e
JOptionPane.showMessageDialog(null, "There are " + ECount + " number of E's and " + eCount + " number of e's in " +sentence); //displays the number of times uppercase and lowercase (E and e) occur in sentence
sentence = JOptionPane.showInputDialog(null, "Type a sentence (type stop to exit"); //prompts user to enter the next sentence
length = sentence.length(); //stores the length of sentence at each iteration of while loop until user enters stop
eCount=0; //resets the counter of lowercase e
ECount=0; } } } //resets the counter of uppercase e
Explanation:
The program uses showInputDialog() method that displays a dialog box on output screen. This dialog box prompts the user to enter a string (sentence) Suppose user enters "Evergreen" as input sentence so
sentence = "Evergreen"
Next the length of this string is computed using length() method and stored in length variable. So
length = sentence.length();
length = 9
The for loop iterates through this input sentence until the variable i is less than length i.e. 9
At first iteration
if (sentence.charAt(i) == 'E') becomes
if (sentence.charAt(0) == 'E')
Here charAt() method is used which returns the character at the specified index i. This if condition is true because the character at 0-th index (first character) of the sentence Evergreen is E. So ECount += 1; statement adds 1 to the count of upper case E so
ECount = 1
At second iteration:
if (sentence.charAt(1) == 'E')
this condition is false because the character at 1st index of sentence is 'v' which not an upper case E so the program moves to next if condition if (sentence.charAt(i) == 'e') which is also false because the character is not a lower case e either.
At third iteration:
if (sentence.charAt(2) == 'E')
this condition is false because the character at 2nd index of sentence is 'e' which not an upper case E so the program moves to next if condition if (sentence.charAt(i) == 'e') which is true because the character is a lower case e. So the statement eCount += 1; executes which adds 1 to the count of e.
eCount = 1
So at each iteration the sentence is checked for an upper case E and lower case e. After the loop breaks, the program moves to the statement:
JOptionPane.showMessageDialog(null, "There are " + ECount + " number of E's and " + eCount + " number of e's in " +sentence);
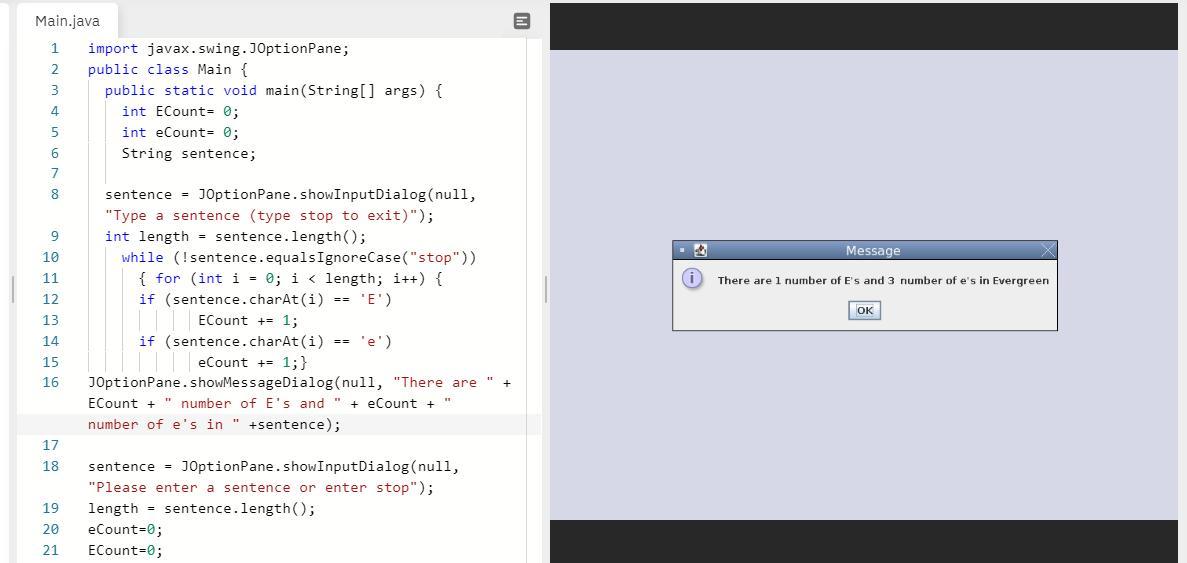
which displays the number of uppercase E and lower case e in a message dialog box. So the output is:
There are 1 number of E's and 3 number of e's in Evergreen.
Then because of while loop user is prompted again to enter a sentence until the user enters "stop". Now the user can enter Stop, StOp, STOp etc. So equalsIgnoreCase method is used to cover all upper/lower case possibilities of the word "stop".
The screenshot of the program and its output is attached.