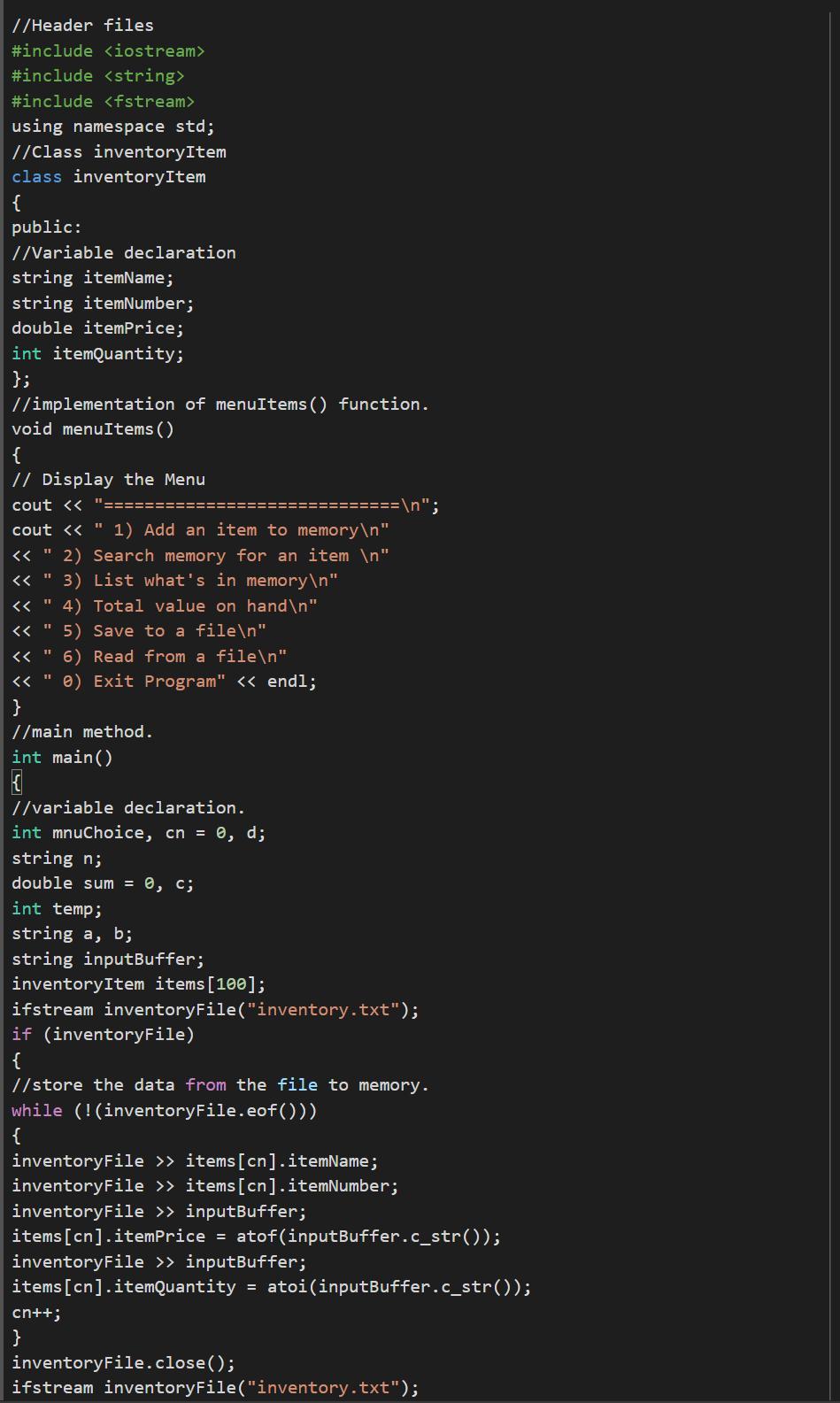
Using the computational language C++ it is possible to write a code is possible to create a function that stores items like this:
<h3>Writting the code in C++: </h3><em>//Header files</em>
<em>#include <iostream></em>
<em>#include <string></em>
<em>#include <fstream></em>
<em>using namespace std;</em>
<em>//Class inventoryItem</em>
<em>class inventoryItem</em>
<em>{</em>
<em>public:</em>
<em>//Variable declaration</em>
<em>string itemName;</em>
<em>string itemNumber;</em>
<em>double itemPrice;</em>
<em>int itemQuantity;</em>
<em>};</em>
<em>//implementation of menuItems() function.</em>
<em>void menuItems()</em>
<em>{</em>
<em>// Display the Menu</em>
<em>cout << "=============================\n";</em>
<em>cout << " 1) Add an item to memory\n"</em>
<em><< " 2) Search memory for an item \n"</em>
<em><< " 3) List what's in memory\n"</em>
<em><< " 4) Total value on hand\n"</em>
<em><< " 5) Save to a file\n"</em>
<em><< " 6) Read from a file\n"</em>
<em><< " 0) Exit Program" << endl;</em>
<em>}</em>
<em>//main method.</em>
<em>int main()</em>
<em>{</em>
<em>//variable declaration.</em>
<em>int mnuChoice, cn = 0, d;</em>
<em>string n;</em>
<em>double sum = 0, c;</em>
<em>int temp;</em>
<em>string a, b;</em>
<em>string inputBuffer;</em>
<em>inventoryItem items[100];</em>
<em>ifstream inventoryFile("inventory.txt");</em>
<em>if (inventoryFile)</em>
<em>{</em>
<em>//store the data from the file to memory.</em>
<em>while (!(inventoryFile.eof()))</em>
<em>{</em>
<em>inventoryFile >> items[cn].itemName;</em>
<em>inventoryFile >> items[cn].itemNumber;</em>
<em>inventoryFile >> inputBuffer;</em>
<em>items[cn].itemPrice = atof(inputBuffer.c_str());</em>
<em>inventoryFile >> inputBuffer;</em>
<em>items[cn].itemQuantity = atoi(inputBuffer.c_str());</em>
<em>cn++;</em>
<em>}</em>
<em>inventoryFile.close();</em>
<em>ifstream inventoryFile("inventory.txt");</em>
<em>ofstream fout;</em>
<em>fout.open("inventory.txt");</em>
<em>do</em>
<em>{</em>
<em>menuItems();</em>
<em>cout << cn << " items stored." << endl;</em>
<em>// Prompt and read choice form the user</em>
<em>cout << "Enter your choice: ";</em>
<em>cin >> mnuChoice;</em>
<em />
<em>switch (mnuChoice)</em>
<em>{</em>
<em>//Add a new inventory item to the data in memory.</em>
<em>case 1:</em>
<em>// Prompt and read name of the item from the user</em>
<em>cout << "Enter name of the item: ";</em>
<em>cin >> inputBuffer;</em>
<em>items[cn].itemName = inputBuffer;</em>
<em>// Prompt and read itemNumber from the user</em>
<em>cout << "Enter the itemNumber: ";</em>
<em>cin >> inputBuffer;</em>
<em>items[cn].itemNumber = inputBuffer;</em>
<em>// Prompt and read itemPrice from the user</em>
<em>cout << "Enter the itemPrice: ";</em>
<em>cin >> inputBuffer;</em>
<em>items[cn].itemPrice = atof(inputBuffer.c_str());</em>
<em>// Prompt and read itemQuantity from the user</em>
<em>cout << "Enter the itemQuantity: ";</em>
<em>cin >> inputBuffer;</em>
<em>items[cn].itemQuantity = atoi(inputBuffer.c_str());</em>
<em>cn++;</em>
<em>break;</em>
<em>//Search the inventory for an item by inventory number.</em>
<em>case 2:</em>
<em>temp = 0;</em>
<em>cout << "Enter inventory itemNumber: ";</em>
<em>cin >> n;</em>
<em>for (int i = 0; i < cn&&temp != 1; i++)</em>
<em>{</em>
<em>// If found, print the stored info</em>
<em>if (items[i].itemNumber.compare(n) == 0)</em>
<em>{</em>
<em>// Display the stored information</em>
<em>cout << "Item Name" << "\t" << "Item Number" << "\t" << " Item Price" << "\t" << " Item Quantity" << endl;</em>
<em>cout << items[i].itemName << "\t " << items[i].itemNumber << " \t" << items[i].itemPrice << "\t " << items[i].itemQuantity << endl;</em>
<em>temp = 1;</em>
<em>}</em>
<em>}</em>
<em>// otherwise print 'not found'.</em>
<em>if (temp == 0)</em>
<em>{</em>
<em>cout << "Not found!!!" << endl;</em>
<em>}</em>
<em>break;</em>
<em>//List the inventory on the screen</em>
<em>case 3:</em>
<em>cout << "The data in the memory is:" << endl;</em>
<em>cout << "Item Name" << "\t" << "Item Number" << "\t" << " Item Price" << "\t" << " Item Quantity" << endl;</em>
<em>for (int i = 0; i < cn; i++)</em>
<em>{</em>
<em>cout << items[i].itemName << "\t " << items[i].itemNumber << "\t " << items[i].itemPrice << " \t" << items[i].itemQuantity << endl;</em>
<em>}</em>
<em>break;</em>
<em>// Calculate the total value on hand.</em>
<em>case 4:</em>
<em>for (int i = 0; i < cn; i++)</em>
<em>{</em>
<em>// The sum is the accumulation of all the (quantities * prices).</em>
<em>sum += items[i].itemPrice*items[i].itemQuantity;</em>
<em>}</em>
<em>cout << "sum value on hand: " << sum << endl;</em>
<em>break;</em>
<em>// Save the inventory data in the given file</em>
<em>case 5:</em>
<em>for (int i = 0; i < cn; i++)</em>
<em>{</em>
<em>if (i == cn - 1)</em>
<em>{</em>
<em />
<em>fout << items[i].itemName << " \t" << items[i].itemNumber << " \t" << items[i].itemPrice << " \t" << items[i].itemQuantity;</em>
<em>}</em>
<em>else</em>
<em>{</em>
<em />
<em>fout << items[i].itemName << " \t" << items[i].itemNumber << " \t" << items[i].itemPrice << " \t" << items[i].itemQuantity << endl;</em>
<em>}</em>
<em>}</em>
<em>break;</em>
<em>// Read the data from the file</em>
<em>case 6:</em>
<em>while (!(inventoryFile.eof()))</em>
<em>{</em>
<em>inventoryFile >> a;</em>
<em>inventoryFile >> b;</em>
<em>inventoryFile >> inputBuffer;</em>
<em>c = atof(inputBuffer.c_str());</em>
<em>inventoryFile >> inputBuffer;</em>
<em>d = atoi(inputBuffer.c_str());</em>
<em>// Dsiplays the data in the file</em>
<em />
<em>cout << a << " " << b << " " << c << " " << d << endl;</em>
<em>}</em>
<em>break;</em>
<em>}</em>
<em>// Check the menu choice is not equal to 0,</em>
<em>//if it is equal exit from the loop</em>
<em>} while (mnuChoice != 0);</em>
<em>// File closed</em>
<em>fout.close();</em>
<em>inventoryFile.close();</em>
<em>}</em>
<em>// If the inventory file does not exist</em>
<em>// and then display the error message.</em>
<em>else</em>
<em>{</em>
<em>cout << "File does not exist!" << endl;</em>
<em>}</em>
<em />
<em>return 0;</em>
<em>}</em>
See more about C++ code at brainly.com/question/17544466
#SPJ1