Answer:
I am writing a JAVA program.
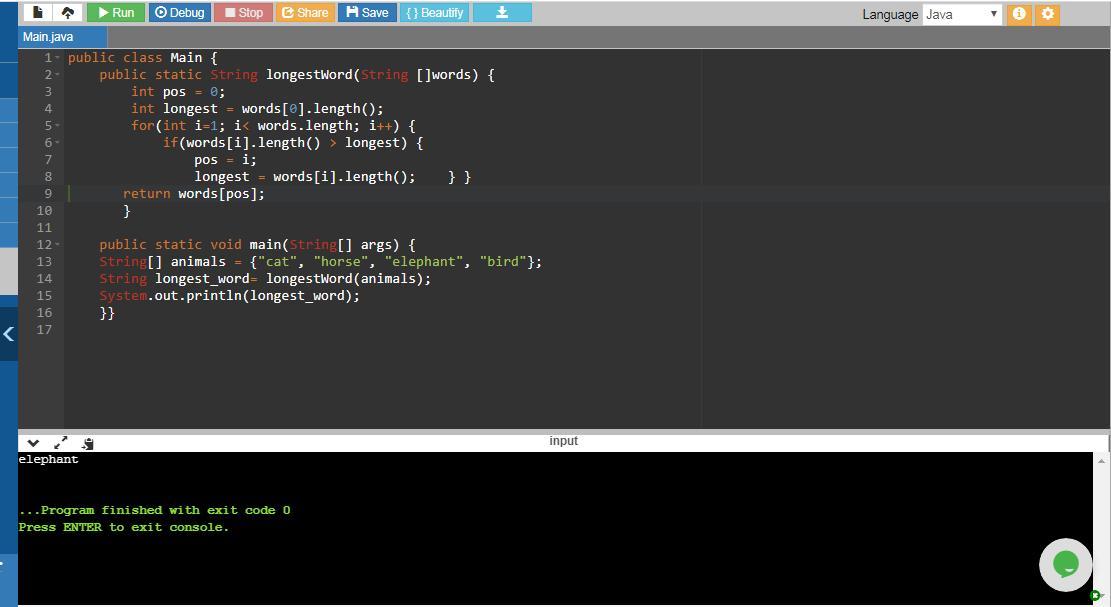
public class StringMethod {
public static String longestWord(String []words) { //method that takes an array "word" of strings and returns the longest string in the array word
int pos = 0; // contains index of the longest word of array words
int longest = words[0].length(); //initially holds the length of the 1st element of words array
for(int i=1; i< words.length; i++) { // iterates through each word of the array until the end of array
if(words[i].length() > longest) { // if the length of word at i-th index of words[] is greater than the length of the word that is contained in longest variable
pos = i; // assigns the index of the longest array element to pos
longest = words[i].length(); } } //assigns the word in words[] array with the longest length to longest variable
return words[pos]; } // returns the longest string in the array
public static void main(String[] args) { //start of main() function body
String[] animals = {"cat", "horse", "elephant", "bird"}; //creates a String type array named animals which has 4 elements/words
String longest_word= longestWord(animals); //calls longestWord method to find the longest string in the array animals and assign that longest string to longest_word.
System.out.println(longest_word); }} //displays the longest word in output
Explanation:
Suppose we have the array of these elements: "cat", "horse", "elephant", "bird" These are four words in the array. Now lets see how the method longestWord() works:
int pos = 0; This variable is initialized to 0.
int longest = words[0].length();
longest holds the length of element at 0th index of words[] array. length() method is used to return the length of the first element words[0] array.
As the first element of array is "cat" so length of cat is 3. Hence longest = 3
for(int i=1; i< words.length; i++)
The loop has a variable i which is initialized to 1. The loop checks if the value of i is less than length of words[] array. The length of words array is 4 as there are 4 elements i.e. cat, horse, elephant and bird in this array. So the condition evaluates to true because i<words.length i.e. 1<4. The body of the loop will execute now. The body of loop contains an if condition if(words[i].length() > longest) which checks if the length of element of array at i-th index is greater than length of the element that is stored in longest variable. As i=1 so word[i] is word[1] which is the second element of words[] array. The second element is horse.
words[i].length() means the length of i-th element of words[] array. So this means words[1].length() i.e. the length of element of words[] at 1st index. The length of horse is 5. So the statement if(words[i].length() > longest) is true because longest=3 and words[1].length() = 5 and 5>3. So the statements of if condition will execute now.
pos = i; this variable pos is used to hold the index position of the longest element in array. So pos = 1 as longest element computed so far is "horse".
longest = words[i].length(); This statement then assigns the length of horse to longest. So now the value of longest = 5
At second iteration i is now 2. Loop condition evaluates to true because i<words.length i.e. 2<4. If condition is also true as i=2 so word[i] is word[2] which is elephant.
words[i].length() now means words[2].length() i.e. the length of element of words[] at 2nd index. The length of elephant is 8. So the statement if(words[i].length() > longest) is true because longest=5 and words[2].length() = 8 and 8>5. So the statements of if condition will execute now.
pos = i; now becomes pos = 2 as longest element computed so far is "elephant".
longest = words[i].length(); This statement then assigns the length of horse to longest. So now the value of longest = 8
At third iteration i is now 3. The loop again checks if the value of i is less than length of words[] array.The condition evaluates to true because i<words.length i.e. 3<4. The body of the loop will execute now. if(words[i].length() > longest) checks if the length of element of array at i-th index is greater than length of the element that is stored in longest variable. As i=3 so word[i] is word[3] which is the fourth element of words[] array. The fourth element is bird.
words[i].length() now means words[3].length() i.e. the length of element of words[] at 3rd index. The length of bird is 4. So the statement if(words[i].length() > longest) is false because longest=8 and words[2].length() = 4 and 4<8. So the statements of if condition will not execute now.
At fourth iteration i is now 4. The loop again checks if the value of i is less than length of words[] array.The condition evaluates to false because i==words.length i.e. 4=4. So the loop breaks.
return words[pos]; statement returns the index position of longest word in words[] array. pos = 2 So the array element at 2nd index is basically the third element of array words[] i.e. elephant. So the longest string in the array is elephant.