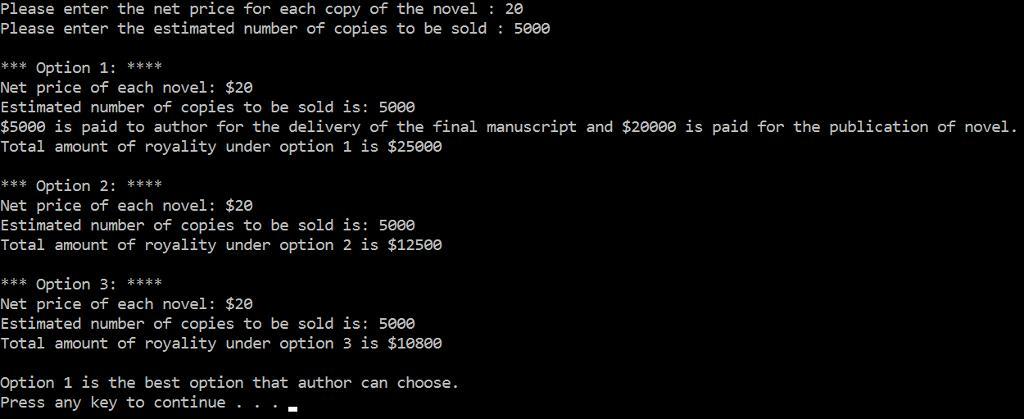
Answer:
Code is given below and output is attached in the diagram:
Explanation:
//Use this header file while using visual studio.
#include "stdafx.h"
//Include the required header files.
#include<iostream>
//Use the standard naming convention.
using namespace std;
//Define a namespace royaltyRates.
namespace royaltyRates
{
//Declare and initialize required named constants.
const double PAY_ON_DELIVERY_OF_NOVAL = 5000;
const double PAY_ON_PUBLISH_OF_NOVAL = 20000;
const double PER_ON_NET_PRICE_SECOND_OPTION =
0.125;
const double PER_ON_NET_PRICE_FIRST_4000 = 0.1;
const double PER_ON_NET_PRICE_OVER_4000 = 0.14;
};
//Start the execution of main() method.
int main()
{
//Declare and initialize the required variables
//which are going to be used to calculate
//royalities under each option.
float net_price;
int num_copies;
float royaltyUnderOption1, royaltyUnderOption2,
royaltyUnderOption3;
royaltyUnderOption1 = royaltyUnderOption2
= royaltyUnderOption3 = 0;
//Prompt the user to enter the net price of each
//novel.
cout << "Please enter the net price for each ";
cout << "copy of the novel : ";
cin >> net_price;
//Prompt the user to enter the estimated number
//of copies of the novels to be sold.
cout << "Please enter the estimated number ";
cout << "of copies to be sold : ";
cin >> num_copies;
//Display the required details and royalty
//calculated under option 1.
cout << "\n*** Option 1: ****" << endl;
cout << "Net price of each novel: $" << net_price;
cout << endl;
cout << "Estimated number of copies to be sold ";
cout << "is: " << num_copies << endl;
cout << "$";
cout << royaltyRates::PAY_ON_DELIVERY_OF_NOVAL;
cout << " is paid to author for the delivery of ";
cout << "the final manuscript and $";
cout << royaltyRates::PAY_ON_PUBLISH_OF_NOVAL;
cout << " is paid for the publication of ";
cout << "novel." << endl;
royaltyUnderOption1 =
royaltyRates::PAY_ON_DELIVERY_OF_NOVAL +
royaltyRates::PAY_ON_PUBLISH_OF_NOVAL;
cout << "Total amount of royalty under option 1 ";
cout << "is $" << royaltyUnderOption1 << endl;
//Display the required details and royalty
//calculated under option 2.
cout << "\n*** Option 2: ****" << endl;
cout << "Net price of each novel: $";
cout << net_price << endl;
cout << "Estimated number of copies to be sold ";
cout << "is: " << num_copies << endl;
royaltyUnderOption2 =
(royaltyRates::PER_ON_NET_PRICE_SECOND_OPTION *
net_price)* num_copies;
cout << "Total amount of royalty under option 2 ";
cout << "is $" << royaltyUnderOption2 << endl;
//Display the required details and royalty
//calculated under option 3.
cout << "\n*** Option 3: ****" << endl;
cout << "Net price of each novel: $" << net_price;
cout << endl;
cout << "Estimated number of copies to be sold ";
cout << "is: " << num_copies << endl;
//If the number of copies is greater than 4000.
if (num_copies > 4000)
{
//Total amount of royalty will be 10% of net
//price of first 4000 copies and 14 % of net
//price of copies sold over 4000.
royaltyUnderOption3 =
(royaltyRates::PER_ON_NET_PRICE_FIRST_4000 *
net_price) * 4000 +
(royaltyRates::PER_ON_NET_PRICE_OVER_4000 *
net_price) * (num_copies - 4000);
}
//Otherwise,
else
{
//Total amount of royalty will be 10% of net
//price of first 4000 copies.
royaltyUnderOption3 =
(royaltyRates::PER_ON_NET_PRICE_FIRST_4000 *
net_price) * num_copies;
}
cout << "Total amount of royalty under option 3 ";
cout << "is $" << royaltyUnderOption3 << endl;
//If the royalty under option 1 is greater than
//royalty under option 2 and 3, then option 1 is
//best option.
if (royaltyUnderOption1 > royaltyUnderOption2 &&
royaltyUnderOption1 > royaltyUnderOption3)
{
cout << "\nOption 1 is the best option that ";
cout << "author can choose." << endl;
}
//If the royalty under option 2 is greater than
//royalty under option 1 and 3, then option 2 is
//best option.
else if (royaltyUnderOption2 > royaltyUnderOption1
&& royaltyUnderOption2 > royaltyUnderOption3)
{
cout << "\nOption 2 is the best option that ";
cout << "author can choose." << endl;
}
//If the royalty under option 3 is greater than
//royalty under option 1 and 2, then option 3 is
//best option.
else
{
cout << "\nOption 3 is the best option that ";
cout << "author can choose." << endl;
}
//Use this command while using visual studio.
system("pause");
return 0;
}