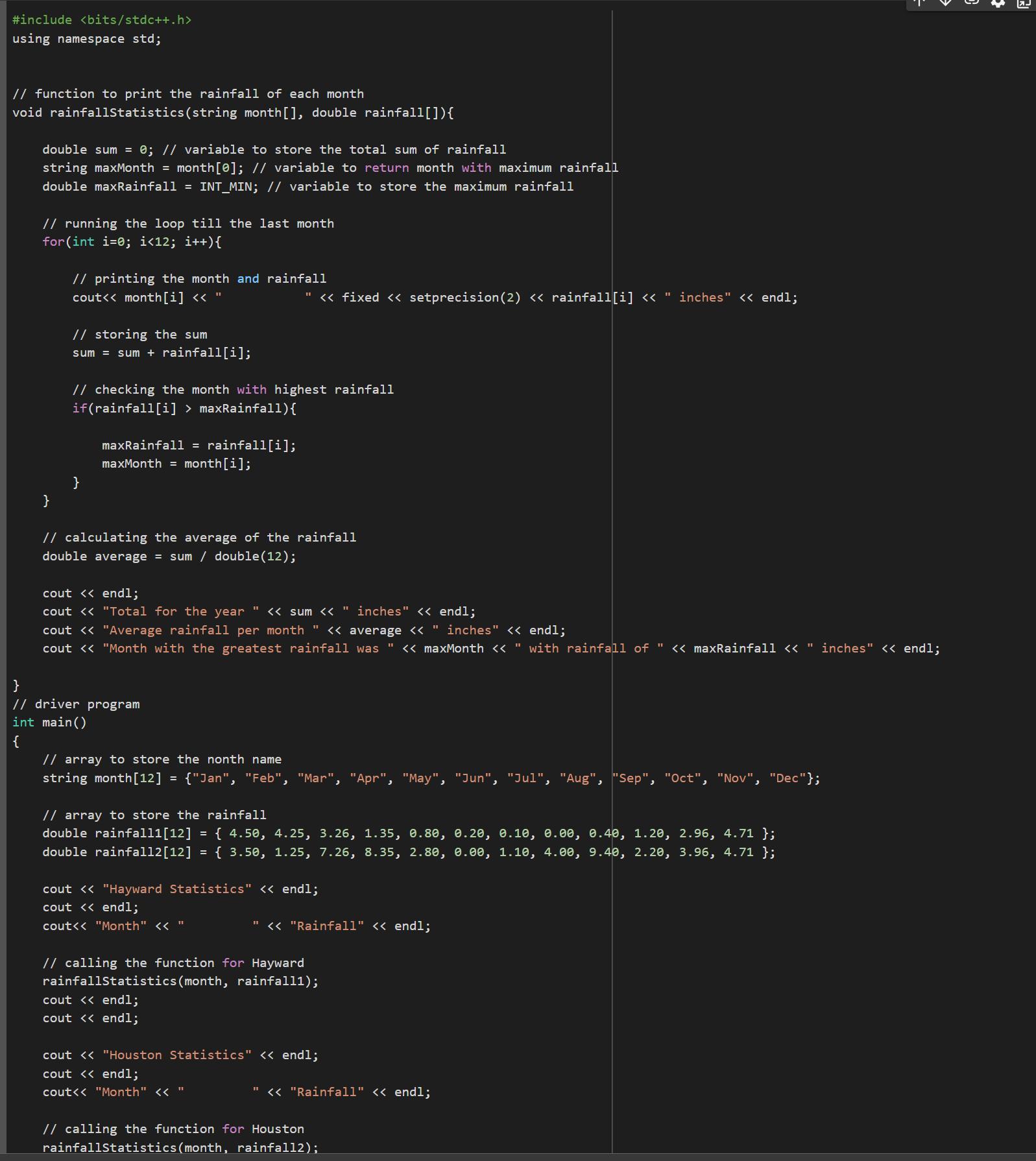
Using the knowledge in computational language in C code it is possible to write a code that print the month name along with their rainfall inches. Then we have to calculate the total rainfall.
<h3>Writting the code:</h3><em>#include <bits/stdc++.h></em>
<em>using </em><em>namespace </em><em>std;</em>
<em />
<em>// function to print the rainfall of each month</em>
<em>void rainfallStatistics(string month[], double rainfall[]){</em>
<em> </em>
<em> double sum = 0; // variable to store the total sum of rainfall</em>
<em> string maxMonth = month[0]; // variable to return month with maximum rainfall</em>
<em> double </em><em>maxRainfall </em><em>= INT_MIN; // variable to store the maximum rainfall</em>
<em> </em>
<em> // running the loop till the last month</em>
<em> for(int i=0; i<12; i++){</em>
<em> </em>
<em> // printing the month and rainfall</em>
<em> cout<< month[i] << " " << fixed << setprecision(2) << rainfall[i] << " inches" << endl;</em>
<em> </em>
<em> // storing the sum</em>
<em> sum = sum + rainfall[i];</em>
<em> </em>
<em> // checking the month with highest rainfall</em>
<em> if(rainfall[i] > </em><em>maxRainfall</em><em>){</em>
<em> </em>
<em> maxRainfall = rainfall[i];</em>
<em> maxMonth = month[i];</em>
<em> }</em>
<em> }</em>
<em> </em>
<em> // calculating the average of the rainfall</em>
<em> double average = sum / double(12);</em>
<em> </em>
<em> cout << endl;</em>
<em> cout << "Total for the year " << sum << " inches" << endl;</em>
<em> cout << "Average rainfall per month " << average << " inches" << endl;</em>
<em> cout << "Month with the greatest rainfall was " << maxMonth << " with rainfall of " << </em><em>maxRainfall </em><em><< " inches" << endl;</em>
<em> </em>
<em>}</em>
<em>// driver program</em>
<em>int main()</em>
<em>{</em>
<em> // array to store the nonth name</em>
<em> string month[12] = {"Jan", "Feb", "Mar", "Apr", "May", "Jun", "Jul", "Aug", "Sep", "Oct", "Nov", "Dec"};</em>
<em> </em>
<em> // array to store the rainfall</em>
<em> double rainfall1[12] = { 4.50, 4.25, 3.26, 1.35, 0.80, 0.20, 0.10, 0.00, 0.40, 1.20, 2.96, 4.71 };</em>
<em> double rainfall2[12] = { 3.50, 1.25, 7.26, 8.35, 2.80, 0.00, 1.10, 4.00, 9.40, 2.20, 3.96, 4.71 };</em>
<em> </em>
<em> cout << "Hayward Statistics" << endl;</em>
<em> cout << endl;</em>
<em> cout<< "Month" << " " << "Rainfall" << endl;</em>
<em> </em>
<em> // calling the function for Hayward</em>
<em> </em><em>rainfallStatistics</em><em>(month, rainfall1);</em>
<em> cout << endl;</em>
<em> cout << endl;</em>
<em> </em>
<em> cout << "Houston Statistics" << endl;</em>
<em> cout << endl;</em>
<em> cout<< "Month" << " " << "Rainfall" << endl;</em>
<em> </em>
<em> // calling the function for Houston</em>
<em> rainfallStatistics(month, rainfall2);</em>
<em> </em>
<em> return 0;</em>
<em>}</em>
See more about c code at brainly.com/question/19705654
#SPJ1