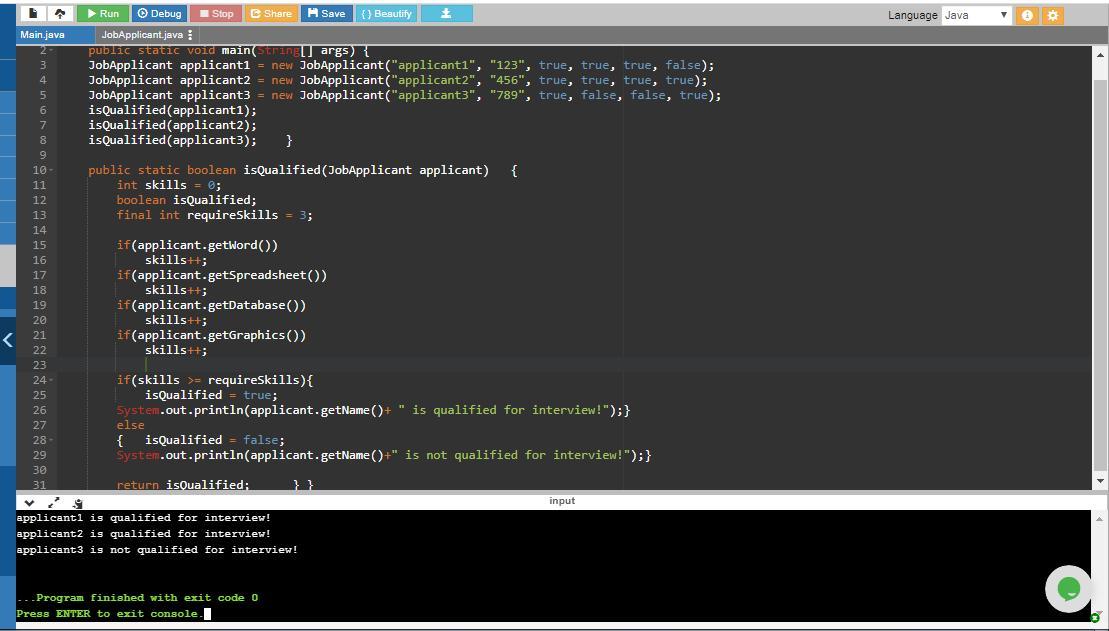
Answer:
// Here is JobApplicant.java
public class JobApplicant { // class name
private String name; // String type private data member/field to hold name of the applicant
private String phoneNum; // String type private data member to hold phone number of the applicant
private boolean word; // boolean private data member to check the word processing skill of applicant
private boolean spreadsheet; // boolean private data member to check the spreadsheets skill of applicant
private boolean database; // boolean private data member to check the database skill of applicant
private boolean graphics; // boolean private data member to check the graphics skill of applicant
public JobApplicant(String name, String phNum, boolean wrd, boolean sprdsht, boolean db, boolean graph){ //parameterized constructor that accepts values for each of the fields
this.name = name;
this.phoneNum = phNum;
this.word = wrd;
this.spreadsheet = sprdsht;
this.database = db;
this.graphics = graph; }
public String getName() { //accessor get method for name field
return name; }
public String getPhoneNum() { //accessor get method for phoneNum field
return phoneNum; }
public boolean getWord() { //accessor get method for word skill
return word; }
public boolean getSpreadsheet() { //accessor method for spreadsheet skill
return spreadsheet; }
public boolean getDatabase() { //accessor get method for database skill
return database; }
public boolean getGraphics() { //accessor get method for graphics skill
return graphics; } }
Explanation:
// Here is the TestJobApplicants.java
public class TestJobApplicants { // class name
public static void main(String[] args) { //start of main() function
JobApplicant applicant1 = new JobApplicant("applicant1", "123", true, true, true, false); //creates object of JobApplicant class named applicant1 and instantiate it by using constructor of JobApplicant. Here the name field is set to applicant1, phoneNum is 123, the skills word, spreadsheet and database is set to true while skill graphics is set to false
JobApplicant applicant2 = new JobApplicant("applicant2", "456", true, true, true, true); //creates another object i.e. applicant2 of JobApplicant class and passes values of each field of the class to the constructor of class
JobApplicant applicant3 = new JobApplicant("applicant3", "789", true, false, false, true); //creates another object for other applicant i.e. applicant23 of JobApplicant class and passes values for each field of the class using constructor of class
isQualified(applicant1); //calls isQualified boolean method by passing object applicant1 to it in order to determine whether applicant is qualified for an interview
isQualified(applicant2); //calls isQualified method to determine whether applicant2 is qualified for an interview
isQualified(applicant3); } //calls isQualified method to determine whether applicant3 is qualified for an interview
public static boolean isQualified(JobApplicant applicant) { //boolean method to determine if applicant is qualified for interview
int skills = 0; //initializes the skills count to 0
boolean isQualified; //boolean variable whose value determines if applicant is qualified for interview
final int requireSkills = 3; //at least 3 skills are required so the maximum value of skills is 3 and this is assigned to requireSkills variable
if(applicant.getWord()) /*The applicant object is used to call method getWord() which returns the current value of word field (true/false) for the current applicant and if condition checks if applicant has word processing skills. */
skills++; //add 1 to the count of skills when above if condition evaluates to true
if(applicant.getSpreadsheet()) //if applicant has spreadsheet skills
skills++; //add 1 to the count of skills
if(applicant.getDatabase()) //if applicant has database skills
skills++; //add 1 to the count of skills
if(applicant.getGraphics()) //if applicant has graphics skills
skills++; //add 1 to the count of skills
if(skills >= requireSkills){ //if the skills count is at least 3 or more
isQualified = true; //value of isQualified is set to true when above if condition evaluates to true which means the user is qualified for interview
System.out.println(applicant.getName()+ " is qualified for interview!");} //displays this message if isQualified is true
else //if the value of skills is less than 3
{ isQualified = false; // isQualified is set to false which means the user is not qualified for interview
System.out.println(applicant.getName()+" is not qualified for interview!");} //displays this message if isQualified is false
return isQualified; } } //returns the value of isQualified (true/false)