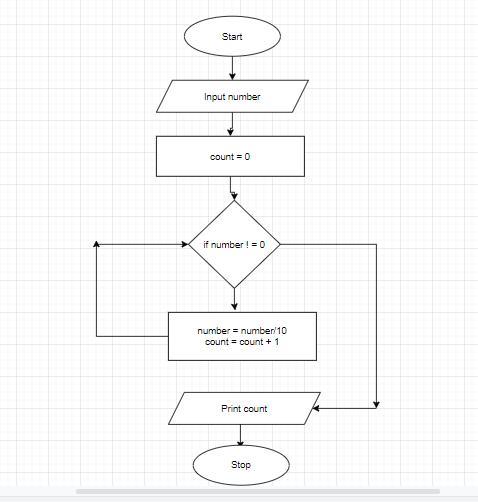
Answer:
Ill do this in C# and Java
Explanation:
C#:
public static void Main(string[] args)
{
string input = Console.ReadLine();
switch (input)
{
case "A1":
Console.WriteLine("Footwear:");
Console.WriteLine("Shoes");
break;
case "B1":
Console.WriteLine("Tops:");
Console.WriteLine("Jackets");
break;
case "C1":
Console.WriteLine("Pants:");
Console.WriteLine("Trousers");
break;
case "A2":
Console.WriteLine("Footwear:");
Console.WriteLine("Trainers");
break;
case "B2":
Console.WriteLine("Tops:");
Console.WriteLine("TShirts");
break;
case "C2":
Console.WriteLine("Pants:");
Console.WriteLine("Shorts");
break;
default:
Console.WriteLine("Incorrect Input");
break;
}
}
Java:
public static void main(String[] args)
{
Scanner myObj = new Scanner(System.in); // Create a Scanner object
String input = myObj.nextLine();
{
switch (input)
{
case "A1":
System.out.println("Footwear:");
System.out.println("Shoes");
break;
case "B1":
System.out.println("Tops:");
System.out.println("Jackets");
break;
case "C1":
System.out.println("Pants:");
System.out.println("Trousers");
break;
case "A2":
System.out.println("Footwear:");
System.out.println("Trainers");
break;
case "B2":
System.out.println("Tops:");
System.out.println("TShirts");
break;
case "C2":
System.out.println("Pants:");
System.out.println("Shorts");
break;
default:
System.out.println("Incorrect Input");
break;
}
}