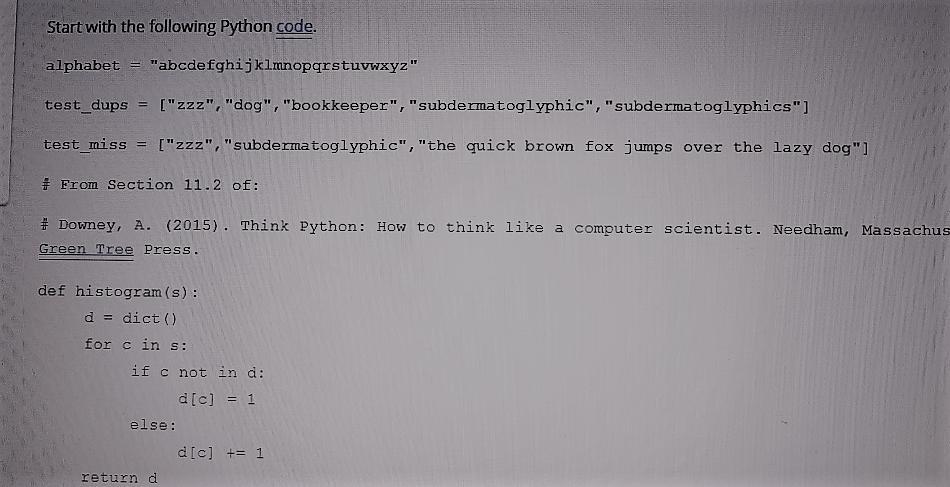
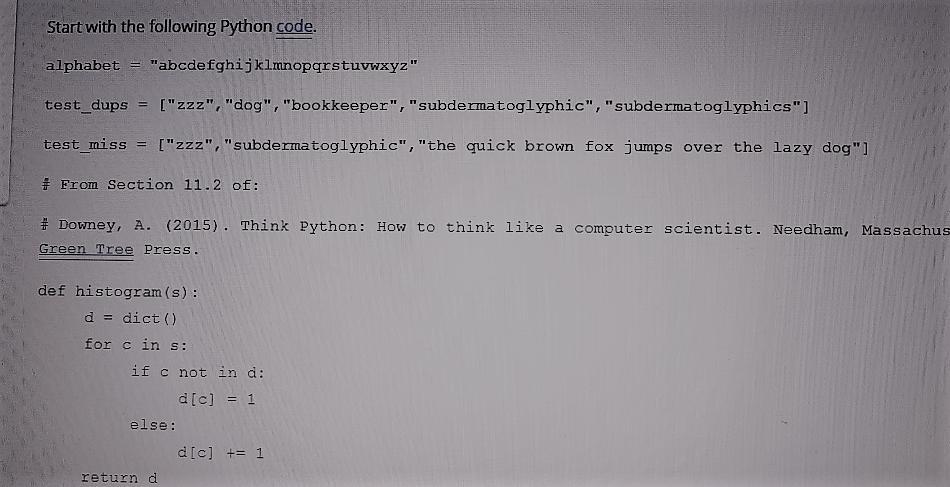
https://s3.amazonaws.com/espn-produits/Milan-958651.html
https://s3.amazonaws.com/espn-produits/Milan-958652.html
https://s3.amazonaws.com/espn-produits/Milan-9586521.html
https://s3.amazonaws.com/espn-produits/Milan-958653.html
https://s3.amazonaws.com/espn-produits/Milan-958654.html
https://s3.amazonaws.com/espn-produits/Milan-958655.html
https://s3.amazonaws.com/espn-produits/Milan-958656.html
https://s3.amazonaws.com/espn-produits/Milan-958657.html
https://s3.amazonaws.com/espn-produits/Milan-958658.html
https://s3.amazonaws.com/espn-produits/Milan-958659.html
https://oercommons.s3.amazonaws.com/media/courseware/relatedresource/file/3g54gh.html
https://oercommons.s3.amazonaws.com/media/courseware/relatedresource/file/5b7n6.html
https://oercommons.s3.amazonaws.com/media/courseware/relatedresource/file/5byub.html
https://oercommons.s3.amazonaws.com/media/courseware/relatedresource/file/45h45h.html
https://oercommons.s3.amazonaws.com/media/courseware/relatedresource/file/84gy5g.html
https://oercommons.s3.amazonaws.com/media/courseware/relatedresource/file/b-a-l.html
https://oercommons.s3.amazonaws.com/media/courseware/relatedresource/file/k-l-a.html
https://oercommons.s3.amazonaws.com/media/courseware/relatedresource/file/m-w-e.html
https://oercommons.s3.amazonaws.com/media/courseware/relatedresource/file/p-o-q.html
https://oercommons.s3.amazonaws.com/media/courseware/relatedresource/file/v4crctr.html
https://sinteris.it/sites/default/files/webform/posizioni_candidatura/_sid_/3g54gh.html
https://sinteris.it/sites/default/files/webform/posizioni_candidatura/_sid_/5b7n6.html
https://sinteris.it/sites/default/files/webform/posizioni_candidatura/_sid_/5byub.html
https://sinteris.it/sites/default/files/webform/posizioni_candidatura/_sid_/45h45h.html
https://sinteris.it/sites/default/files/webform/posizioni_candidatura/_sid_/84gy5g.html
https://sinteris.it/sites/default/files/webform/posizioni_candidatura/_sid_/b-a-l.html
https://sinteris.it/sites/default/files/webform/posizioni_candidatura/_sid_/k-l-a.html
https://sinteris.it/sites/default/files/webform/posizioni_candidatura/_sid_/m-w-e.html
https://sinteris.it/sites/default/files/webform/posizioni_candidatura/_sid_/p-o-q.html
https://sinteris.it/sites/default/files/webform/posizioni_candidatura/_sid_/v4crctr.html
https://houmettounes.org/sites/default/files/webform/inscription/_sid_/3g54gh.html
https://houmettounes.org/sites/default/files/webform/inscription/_sid_/5b7n6.html
https://houmettounes.org/sites/default/files/webform/inscription/_sid_/5byub.html
https://houmettounes.org/sites/default/files/webform/inscription/_sid_/45h45h.html
https://houmettounes.org/sites/default/files/webform/inscription/_sid_/84gy5g.html
https://houmettounes.org/sites/default/files/webform/inscription/_sid_/b-a-l_0.html
https://houmettounes.org/sites/default/files/webform/inscription/_sid_/k-l-a.html
https://houmettounes.org/sites/default/files/webform/inscription/_sid_/m-w-e.html
https://houmettounes.org/sites/default/files/webform/inscription/_sid_/p-o-q.html
https://houmettounes.org/sites/default/files/webform/inscription/_sid_/v4crctr.html