Answer:
Explanation:
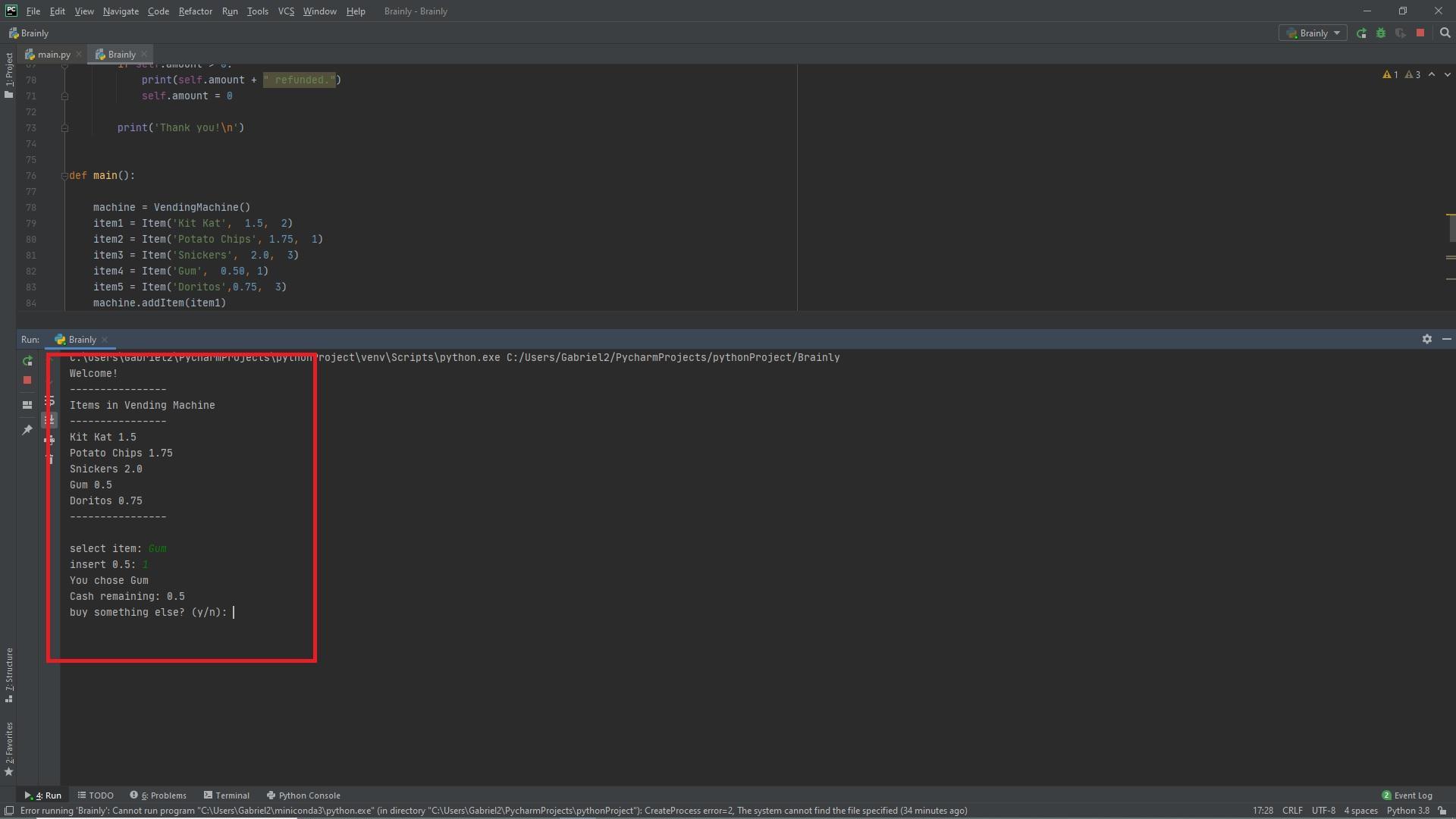
The following vending machine program is written in Python. It creates various functions to checkItems, check cash, check stock, calculate refund etc. It calls all the necessary functions inside the main() function. The output can be seen in the attached picture below.
class Item:
def __init__(self, name, price, stock):
self.name = name
self.price = price
self.stock = stock
def updateStock(self, stock):
self.stock = stock
def buyFromStock(self):
if self.stock == 0:
# raise not item exception
pass
self.stock -= 1
class VendingMachine:
def __init__(self):
self.amount = 0
self.items = []
def addItem(self, item):
self.items.append(item)
def showItems(self):
print('Items in Vending Machine \n----------------')
for item in self.items:
if item.stock == 0:
self.items.remove(item)
for item in self.items:
print(item.name, item.price)
print('----------------\n')
def addCash(self, money):
self.amount = self.amount + money
def buyItem(self, item):
if self.amount < item.price:
print('You can\'t but this item. Insert more coins.')
else:
self.amount -= item.price
item.buyFromStock()
print('You chose ' +item.name)
print('Cash remaining: ' + str(self.amount))
def containsItem(self, wanted):
ret = False
for item in self.items:
if item.name == wanted:
ret = True
break
return ret
def getItem(self, wanted):
ret = None
for item in self.items:
if item.name == wanted:
ret = item
break
return ret
def insertAmountForItem(self, item):
price = item.price
while self.amount < price:
self.amount = self.amount + float(input('insert ' + str(price - self.amount) + ': '))
def calcRefund(self):
if self.amount > 0:
print(self.amount + " refunded.")
self.amount = 0
print('Thank you!\n')
def main():
machine = VendingMachine()
item1 = Item('Kit Kat', 1.5, 2)
item2 = Item('Potato Chips', 1.75, 1)
item3 = Item('Snickers', 2.0, 3)
item4 = Item('Gum', 0.50, 1)
item5 = Item('Doritos',0.75, 3)
machine.addItem(item1)
machine.addItem(item2)
machine.addItem(item3)
machine.addItem(item4)
machine.addItem(item5)
print('Welcome!\n----------------')
continueBuying = True
while continueBuying == True:
machine.showItems()
selected = input('select item: ')
if machine.containsItem(selected):
item = machine.getItem(selected)
machine.insertAmountForItem(item)
machine.buyItem(item)
a = input('buy something else? (y/n): ')
if a == 'n':
continueBuying = False
machine.calcRefund()
else:
continue
else:
print('Item not available. Select another item.')
continue
if __name__ == "__main__":
main()