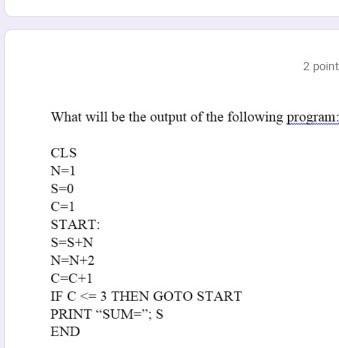
Answer:
I've updated the Account class as per the instructions. The instructions mention "the constructor for this class creates a random account number" although I didn't find where that was. As a result, I created a simple method to generates the account number (located at the bottom of the class). Be sure you understand the changes (highlighted in yellow) and feel free to ask follow-up questions:
Explanation:
//*******************************************************
// Account.java
//
// A bank account class with methods to deposit to, withdraw from,
// change the name on, and get a String representation
// of the account.
//*******************************************************
import java.util.Random; // Used for Random # generator
public class Account
{
private double balance;
private String name;
private long acctNum;
//----------------------------------------------
//Constructor -- initializes balance, owner, and account number
//----------------------------------------------
public Account(double initBal, String owner, long number)
{
balance = initBal;
name = owner;
acctNum = number;
}
// !!!!!! New Constructor !!!!!!
public Account(double initBal, String owner)
{
balance = initBal;
name = owner;
acctNum = generateAccountNumber();
}
// !!!!!! New Constructor !!!!!!
public Account(String owner)
{
balance = 0;
name = owner;
acctNum = generateAccountNumber();
}
//----------------------------------------------
// Checks to see if balance is sufficient for withdrawal.
// If so, decrements balance by amount; if not, prints message.
//----------------------------------------------
public void withdraw(double amount)
{
if (balance >= amount)
balance -= amount;
else
System.out.println("Insufficient funds");
}
// !!!!!! New withdraw() method !!!!!!
public void withdraw(double amount, double fee)
{
double amountWithFee = amount + fee;
if (balance >= amountWithFee)
balance -= amountWithFee;
else
System.out.println("Insufficient funds");
}
//----------------------------------------------
// Adds deposit amount to balance.
//----------------------------------------------
public void deposit(double amount)
{
balance += amount;
}
//----------------------------------------------
// Returns balance.
//----------------------------------------------
public double getBalance()
{
return balance;
}
//----------------------------------------------
// Returns a string containing the name, account number, and balance.
//----------------------------------------------
public String toString()
{
return "Name:" + name +
"\nAccount Number: " + acctNum +
"\nBalance: " + balance;
}
// !!!! NEW PRIVATE HELPER METHOD TO GENERATE ACCOUNT NUMBERS !!!!!
//-------------------------------------------------------
// Returns a random account number between 10000 - 99999
//--------------------------------------------------------
private long generateAccountNumber()
{
Random r = new Random(); // Seed the random number genertor with the system time
return 10000 + r.nextInt(89999); // .nextInt(89999) will return a value between 0 and 89999)
}
}