Answer:
Here is the JAVA program:
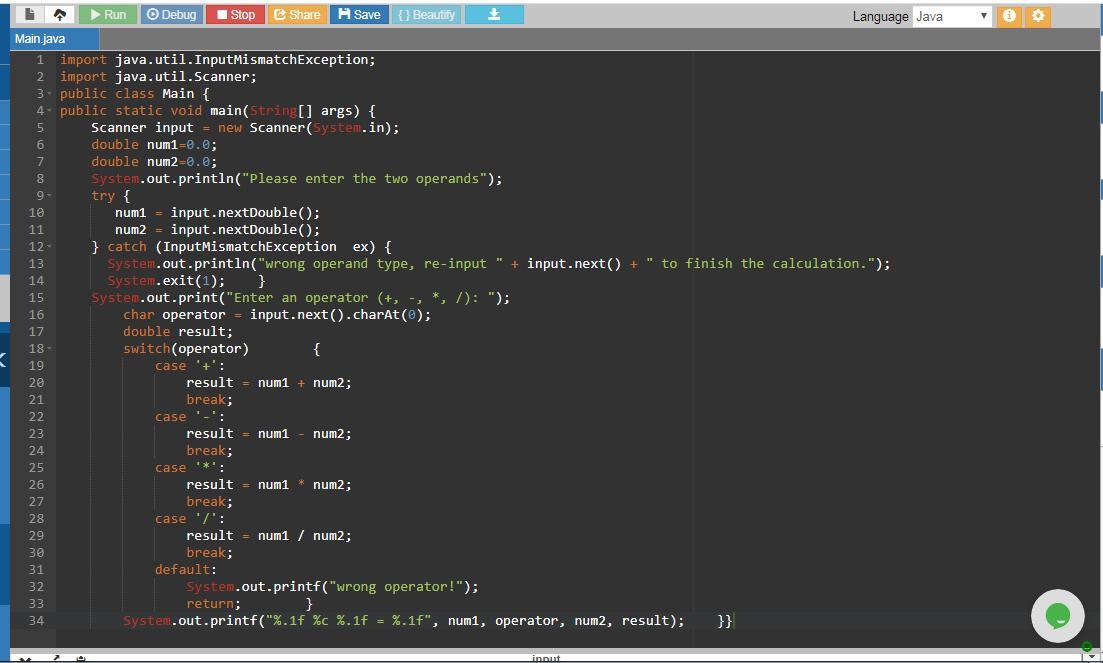
import java.util.InputMismatchException; // exception that is thrown when input does not match the expected type
import java.util.Scanner; //used to take input from user
public class Main {
public static void main(String[] args) { //start of main function
Scanner input = new Scanner(System.in); // creates Scanner class object
double num1=0.0; // double type operand 1
double num2=0.0; // double type operand 2
System.out.println("Please enter 2 operands"); //prompts user to enter two operands
try { //defines a chunk of code to be tested for non numeric operand error
num1 = input.nextDouble(); //reads operand 1 value
num2 = input.nextDouble(); //reads operand 2 value
} catch (InputMismatchException ex) { //code chunk executed when exception occurs in program
System.out.println("wrong operand type, re-input " + input.next() + " to finish the calculation."); //displays wrong operand type if user enters non numeric operands
System.exit(1); }//exits the program
System.out.print("Enter an operator (+, -, *, /): "); //prompts user to enter an operator
char operator = input.next().charAt(0); //reads the input operator
double result; // to store the result of the operation
switch(operator) { //decided operation on basis of input operator
case '+': // if user enters + operator
result = num1 + num2; //adds two operands
break;
case '-': // if user enters - operator
result = num1 - num2; //subtracts two operands
break;
case '*': // if user enters * operator
result = num1 * num2; //multiplies two operands
break;
case '/': // if user enters / operator
result = num1 / num2; //divided two operands
break;
default: //if user enters wrong operator
System.out.printf("wrong operator!"); //displays wrong operator
return; }
System.out.printf("%.1f %c %.1f = %.1f", num1, operator, num2, result); }} //displays the result of the operation
Explanation:
The program is well explained in the comments mentioned with each line of program. The user is prompted to enter the values of two operands num1 and num2. The try block is used to test for non numeric operand error and throws InputMismatchException when any of the input operands (num1 or num2) is non numeric. InputMismatchException is thrown by Scanner class. This informs that the token retrieved (which is the num1 or num2 operand) does not match the expected type (which is type numeric). When this error occurs in the program, catch block is used to execute a code chunk, which is the print statement in this program. The print statement informs the user of the wrong operand type before exiting. It also asks the user to re-input the number to finish the calculation and the wrong input type is also mentioned in the output that is to be re-input.
If you want the program to take the input again from user after throwing this exception then you can alter the above program by using two try catch blocks separately for the two operands:
//for operand 1 i.e. num1
System.out.println("Please enter operand 1: ");
try {
num1 = input.nextDouble();
} catch (InputMismatchException ex) {
System.out.println("wrong operand type, re-input " + input.next() + " to finish the calculation.");
num1 = input.nextDouble(); } //reads input of operand 1 again from user
//for operand 2 i.e. num2
System.out.println("Please enter operand 2: ");
try {
num2 = input.nextDouble();
} catch (InputMismatchException ex) {
System.out.println("wrong operand type, re-input " + input.next() + " to finish the calculation.");
num2 = input.nextDouble(); } //reads input of operand 1 again from user
The program and its output is attached.