Answer:
Here is the C++ program that simulates lottery:
#include<iostream> //to use input output functions
using namespace std; //to access objects cin cout
int main(){ //start of main function
int size= 5; // size of arrays
int range = 10; //range of random numbers from 0 to 9
int user[size]; // user array
int lottery[size]; // lottery array
for(int i=0;i<size;i++) //iterates through the array
lottery[i]=rand()%range; // generates random number in specified range
cout<<"Enter "<<size<<" digits: "; //prompts user to enter 5 digits
for(int i=0;i<size;i++) //loops through the user array
cin>>user[i]; //reads input digits from user
int match=0; //stores number of matching digits
for(int i=0;i<size;i++) //iterates through array to compare user and lottery arrays
if(user[i]==lottery[i]) //if digit at i-th index of user array matches to that of lottery array
match++; //increments count of matching digits by 1
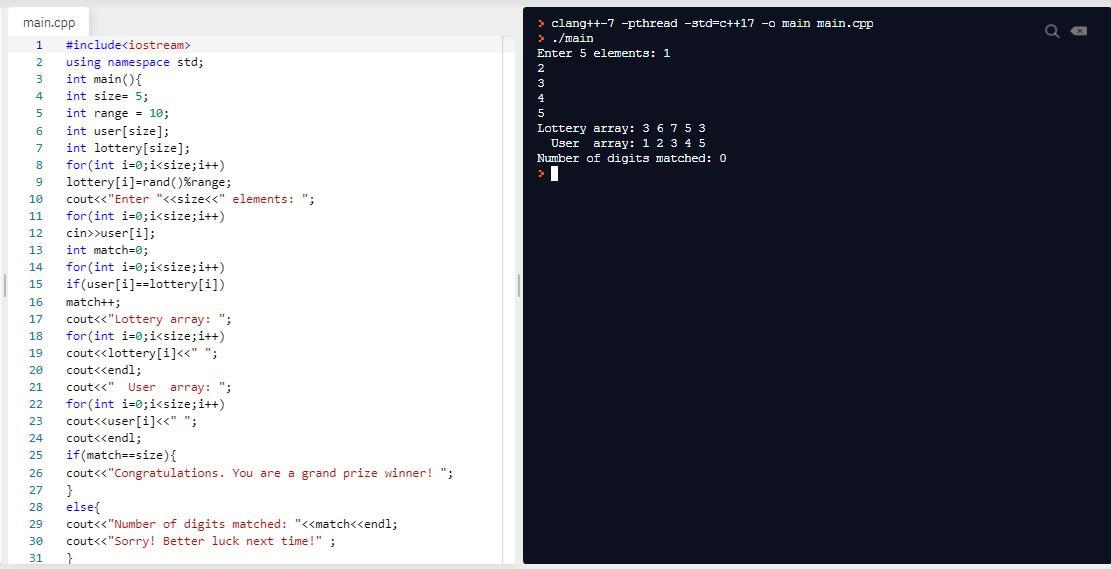
cout<<"Lottery array: "; // display digits of lottery array
for(int i=0;i<size;i++) //iterates through elements of lottery array
cout<<lottery[i]<<" "; //prints elements of lottery array with a space between them
cout<<endl; //prints a new line
cout<<" User array: "; // prints digits of user array
for(int i=0;i<size;i++) //iterates through elements of user array
cout<<user[i]<<" "; //prints elements of user array
cout<<endl; // prints a new line
if(match==size){ //if all the digits match
cout<<"Congratulations. You are a grand prize winner! "; }//displays this message proclaiming the user as a grand prize winner
else{ // if all digits of user array do not match with lottery array digits
cout<<"Number of digits matched: "<<match<<endl; //displays the number of matched digits
cout<<"Sorry! Better luck next time!" ; //displays this message when all digits don't match
}
}
Explanation:
If you want to keep the size and range fixed then you can use #define before the main() function to give a constant value to size and range as:
#define size 5
#define range 10
The program uses rand() function in order to generate random numbers for lottery array in the range of 0 through 9.
Then the program declares a user array with size = 5 and prompts user to enter 5 digits to stores in user array.
Next the program matches each digit of user array to the corresponding digit of lottery array and if the two digits match then the program increments the match variable by 1 to count the matched digits. For example, lets say lottery has the following elements:
lottery: 7,4,9,1,3
Lets say user array has following elements input by user at console
user: 4,2,9,7,3
Now at first iteration the digit 7 at 0-th index of lottery array is matched to the digit 4 at 0-th index of user array. This index is specified using variable i. These means the first element of lottery array is matched with first element of user array. As these digits are not equal so they don't match and the variable i is incremented to point to the position of next digit.
Now at second iteration the digit 4 in lottery array is matched to the digit 2 of user array. As these digits are not equal so they don't match and the variable i is incremented.
at third iteration the digit 9 in lottery array is matched to the digit 9 of user array. As these digits equal so they match and the variable match is incremented to 1 in order to count the number of matches. So value of match = 1
Now at fourth iteration the digit 1 in lottery array is matched to the digit 7 of user array. As these digits are not equal so they don't match and the variable i is incremented. The value of match also remains the same i.e. 1
at fifth iteration the digit 3 in lottery array is matched to the digit 3 of user array. As these digits equal so they match and the variable match is incremented to 1 in order to count the number of matches. So value of match = 2
Next the loop ends because the value of exceeds 5 which is the size of the array.
Next if(match==size) statement has an if condition which checks if all digits match. This is checked by comparing the count of match variable to the size of the array. The value of match is 2 and value of size is 5 so this means that all the digits do not match. Hence this condition evaluates to false. So the statement in if part will not execute and program moves to the statement: cout<<"Number of digits matched: "<<match<<endl; which displays the value of match variable i.e. 2 as:
Number of digits matched: 2
followed by statement cout<<"Sorry! Better luck next time!" ; which displays the message:
Sorry! Better luck next time!