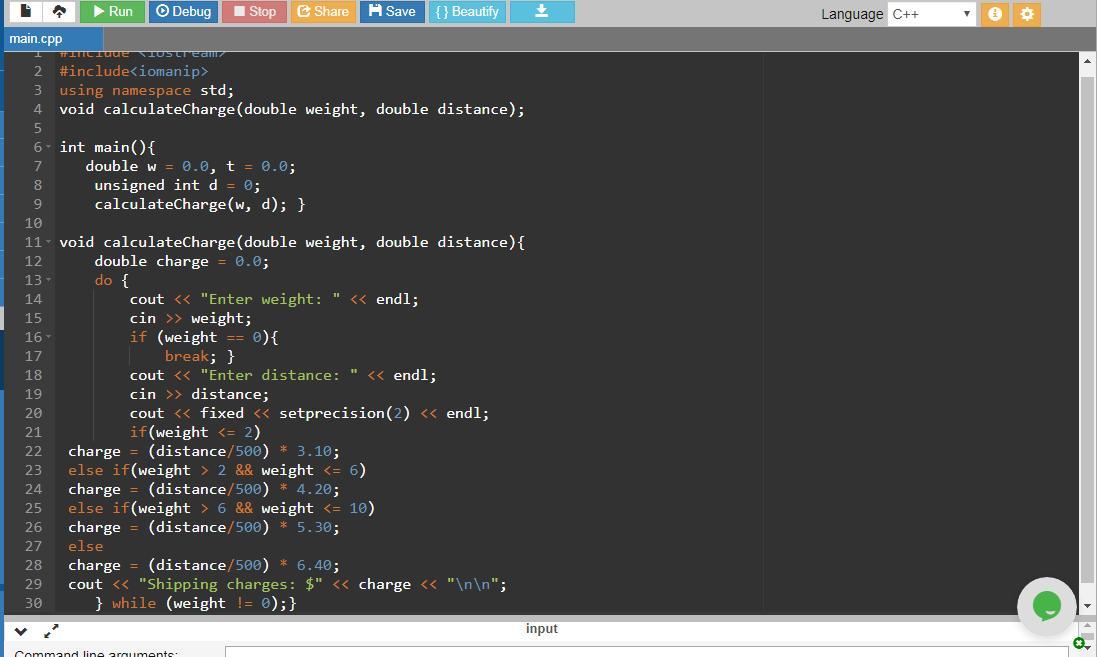
Answer:
I am writing a C++ program:
#include <iostream> //to use input output functions
#include<iomanip> // to format the output
using namespace std; // to identify objects like cin cout
void calculateCharge(double weight, double distance); // function prototype
int main(){ //start of main() function body
double w = 0.0, t = 0.0; // w variable is for weight and t is for total
unsigned int d = 0; // d variable is to hold the value of distance
calculateCharge(w, d); } //calls calculateCharge method by passing weight and distance values to this method
void calculateCharge(double weight, double distance){ //method that takes weight and distance as parameters and compute the shipping charge
double charge = 0.0; //to store the value of shipping charges
do { // do while loop to handle multiple packages until a weight of 0 is entered
cout << "Enter weight: " << endl; //prompts user to enter weight
cin >> weight; //reads the input weight value
if (weight == 0){ // if the value of weight is equal to 0
break; } // the loop breaks if value of weight is 0
cout << "Enter distance: " << endl; // if value of weight is not zero then the program precedes by prompting user to enter the value of distance
cin >> distance; //reads the input distance value
cout << fixed << setprecision(2) << endl; //set the precision to 2 means the sets the number of digits of an output to 2 decimal places
if(weight <= 2) //if the value of weight is less than or equals to 2
charge = (distance/500) * 3.10; //compute the charge by this formula
else if(weight > 2 && weight <= 6) //if weight is over 2 kg but not more than 6 kg
charge = (distance/500) * 4.20; //charge is computed by multiplying value of distance to that of weight and if distance is greater than 500 then it is divided by 500 first
else if(weight > 6 && weight <= 10) // if weight is over 6 kg but not more than 10 kg
charge = (distance/500) * 5.30; //compute shipping charges by this formula
else //if weight is over 10 kg
charge = (distance/500) * 6.40; // compute shipping charge by multiplying value of distance to that of 6.40 weight value and if distance is greater than 500 then distance is divided by 500 first
cout << "Shipping charges: $" << charge << "\n"; //display the computed shipping charge
} while (weight != 0); //the loop continues to execute until weight 0 is entered
}
Explanation:
The program is explained in the comments mentioned above. The program has a main() function that declares variable for weight, distance and total and then calls calculateCharge() method passing weight and dsitance in order to compute and return the shipping charge.
In calculateCharge() the user is prompted to enter the values for weight and distance. Then the based on the value of weight , the shipping charge is computed. Shipping charge is computed by multiplying the weight with distance. The distance is assumed to be 500 but if the distance entered by user exceeds 500 then the distance value is divided by 500 and then multiplied by the specified weight (according to if or else if conditions) in order to compute shipping charge. The program has a do while loop that keeps taking input from user until the user enters 0 as the value of weight.
The screenshot of the program and its output is attached.