Answer:
Here is the Location class:
public class Location { //class name
public int row; // public data field to hold the value of no. of rows
public int column; // public data field to hold the value of no. of columns
public double maxValue; //public data field to hold the maximum value
public Location(int row, int column, double maxValue) { //parameterized constructor of Location class
//this keyword is used to refer to a current instance variable and used to avoid naming conflicts between attributes and parameters with the same name
this.row = row;
this.column = column;
this.maxValue = maxValue; }
public static Location locateLargest(double[][] a) { //method that takes a 2 dimensional array a as argument and returns the location of the largest element
int row = 0; //initializes row to 0
int column = 0; //initializes column to 0
double maxValue = a[row][column]; //stores largest element
for (int i = 0; i < a.length; i++) { //iterates through rows of a[] array
for (int j = 0; j < a[i].length; j++) { //iterates through columns of array
if (maxValue < a[i][j]) { //if the maxValue is less than the element of 2 dimensional array at ith row and jth column
maxValue = a[i][j]; //then set that element to maxValue
row = i; // i is set to traverse through rows
column = j; } } } // i is set to move through columns
return new Location(row,column,maxValue); } } //calls constructor of class by passing row, column and maxValue as argument
Explanation:
Here is the Main class with a main() function to test program
import java.util.Scanner; //to accept input from user
public class Main { //class name
public static void main(String[] args) { //start of main function
Scanner scan = new Scanner(System.in); //creates Scanner class object to scan the input from user
System.out.print("Enter the number of rows and columns in the array: "); //prompt for user
int row = scan.nextInt(); // reads value of row from user
int column = scan.nextInt(); //reads input value of column
double[][] array = new double[row][column]; //declares a 2 dimensional array named array
System.out.println("Enter the array:"); //prompts to enter array elements
for (int i = 0; i < array.length; i++) { //iterates through the rows of array until the size of array is reaced
for (int j = 0; j < array[i].length; j++) { //iterates through the columns of array
array[i][j] = scan.nextDouble(); } } //reads each element at i-th row and j-th column
Location location = Location.locateLargest(array); //calls locateLargest method by passing array to it in order to locate the largest element in the array
System.out.println("The largest element in a two-dimensional array is: " + location.maxValue); //displays the largest element of array
System.out.println("The location of the largest element is at (" + location.row + ", " + location.column + ")"); } } //displays the location of the largest element in the two dimensional array
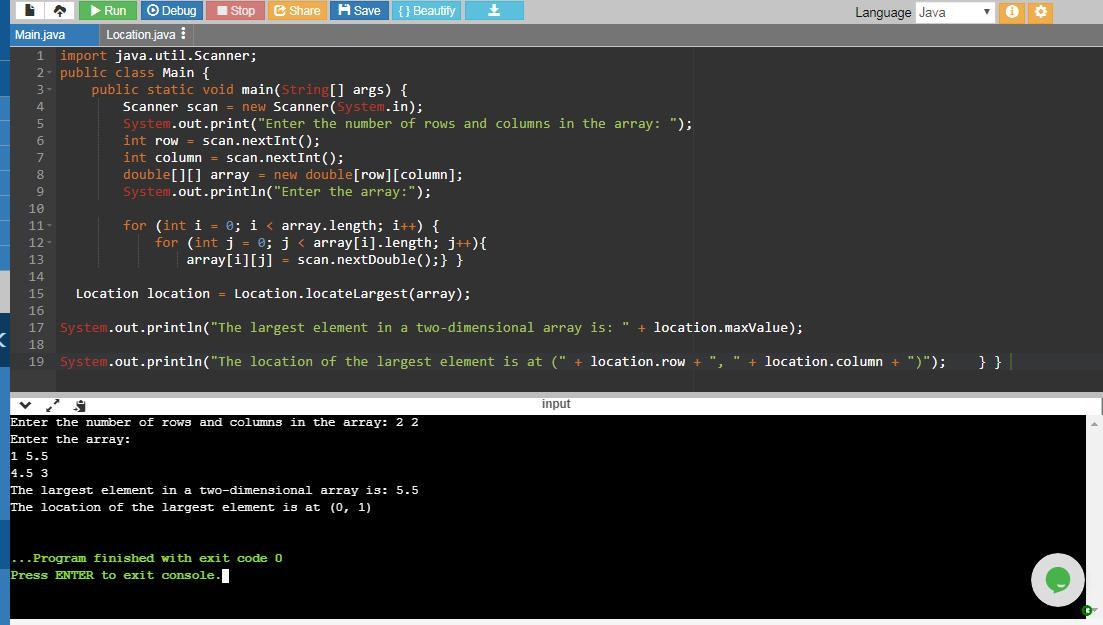
Suppose the user enters 2 rows and 2 columns. The elements are:
1 5.5
4.5 3
The program works as follows:
for (int i = 0; i < array.length; i++) this outer loop iterates through rows
i = 0
inner loop for (int j = 0; j < array[i].length; j++) iterates through columns
array[i][j] = scan.nextDouble(); reads the element at position i-th row and j-th column. This becomes:
array[0][0] = scan.nextDouble();
so element at 0th row and 0th column is 1
Location location = Location.locateLargest(array); now this calls the method which works as follows:
double maxValue = a[row][column]; this becomes:
double maxValue = a[0][0];
so maxValue = 1
for (int i = 0; i < a.length; i++) this loop in method iterates through rows and for (int j = 0; j < a[i].length; j++) this iterates through columns of array
if (maxValue < a[i][j]) this becomes:
if (maxValue < a[0][0])
As we know that maxValue = 1 so this if condition is true.
maxValue = a[i][j]; this becomes:
maxValue = a[0][0];
maxValue = 1
Now set row = 0 and column = 0
Now the inner loop value of j is incremented to 1. So j = 1
At next iteration array[0][1] is checked. The element at this position is 5.5
if (maxValue < a[i][j]) is true because 1<5.5 so now value of maxValue becomes:
maxValue = 5.5
and
i = 0 j = 1
This way at each iteration of inner loop the columns are traversed and at each iteration of outer loop rows are traversed.
At next iteration element at array[1][0] is checked which is 4.5. This is not greater than maxValue so maxValue remains 5.5
At next iteration element at array[1][1] is checked which is 3. This is not greater than maxValue so maxValue remains 5.5 .
After both the loops end the statement:
return new Location(row,column,maxValue);
returns row , column and maxValue
where row = 0 column = 1 and maxValue = 5.5
So the output is:
The largest element in a two-dimensional array is: 5.5
The location of the largest element is at (0,1)