Answer:
Check the explanation
Explanation:
note: code is implemented as per the main method provided:
code:
using System;
public class Package
{
string senderName11;
string senderAddress1;
string senderCity1;
string senderState1;
string senderZip1;
string recipientName1;
string recipientAddress1;
string recipientCity1;
string recipientState1;
string recipientZip1;
decimal weight1;
decimal costPerOunce1;
public string SenderName11
{
get { return senderName11; }
set { senderName11 = value; }
}
public string SenderAddress1
{
get { return senderAddress1; }
set { senderAddress1 = value; }
}
public string SenderCity1
{
get { return senderCity1; }
set { senderCity1 = value; }
}
public string SenderState1
{
get { return senderState1; }
set { senderState1 = value; }
}
public string SenderZip1
{
get { return senderZip1;}
set { senderZip1 = value; }
}
public string RecipientName1
{
get { return recipientName1; }
set { recipientName1 = value; }
}
public string RecipientAddress1
{
get { return recipientAddress1; }
set { recipientAddress1 = value; }
}
public string RecipientCity1
{
get { return recipientCity1; }
set { recipientCity1 = value; }
}
public string RecipientState1
{
get { return recipientState1; }
set { recipientState1 = value; }
}
public string RecipientZip1
{
get { return recipientZip1; }
set { recipientZip1 = value; }
}
public decimal Weight1
{
get { return weight1; }
set
{
if (value > 0)
weight1 = value;
else
Console.WriteLine("Weight1 can't be less tha zero");
}
}
public decimal CostPerOunce1
{
get { return costPerOunce1; }
set
{
if (value > 0)
costPerOunce1 = value;
else
Console.WriteLine("Cost per ounce can't be less than zero");
)
{
SenderName11 = senderName11;
SenderAddress1 = senderAddress1;
)
{
TwoDayDeliveryFee = twoDayDeliveryFee;
}
public override decimal CalculateCost()
{
return base.CalculateCost() + TwoDayDeliveryFee;
}
OvernightDeliveryFeePerOunce = overnightDeliveryFeePerOunce;
}
public override decimal CalculateCost()
{
return (CostPerOunce1 + OvernightDeliveryFeePerOunce) * Weight1;
}
}
class TestPackages
{
static void Main(string[] args)
{
Package regularPackage = new Package
(
"Peter Anderson",
"123 Main St, Ashville, NC 27111 ",
"Ashville",
"NC 27111",
"MN 55416",
"Mary Brown",
"456 Broad St Benson, NC 27222",
"St. Petersburg",
"Benson",
"NC 27222",
160M,
0.1M
);
Console.WriteLine("\nRegular Package: ");
Console.WriteLine(" Sender's Name: {0}",
regularPackage.SenderName11);
Console.WriteLine(" Sender's Address: {0}",
regularPackage.SenderAddress1);
Console.WriteLine(" Recipient's Name: {0}",
regularPackage.RecipientName1);
Console.WriteLine(" Recipient's Address: {0}",
regularPackage.RecipientAddress1);
Console.WriteLine(" Weight1: {0}"
, regularPackage.Weight1);
Console.WriteLine(" Cost Per Ounce: {0:C}",
regularPackage.CostPerOunce1);
Console.WriteLine("Shipping Cost: {0:C}",
regularPackage.CalculateCost());
Console.WriteLine(regularPackage.CalculateCost());
TwoDayPackage twoDayPackage = new TwoDayPackage
(
"Peter Anderson",
"123 Main St 123 Main St, Ashville, NC 27111",
"Ashville",
"NC 27111",
"MN 55416",
"Mary Brown",
"456 Broad St",
"St. Petersburg",
"Benson",
"NC 27222",
160M,
0.1M,
1.5M
);
Console.WriteLine("\nTwo-Day Package: ");
Console.WriteLine(" Sender's Name: {0}",
twoDayPackage.SenderName11);
Console.WriteLine(" Sender's Address: {0}",
twoDayPackage.SenderAddress1);
Console.WriteLine(" Recipient's Name: {0}",
twoDayPackage.RecipientName1);
Console.WriteLine(" Recipient's Address: {0}",
twoDayPackage.RecipientAddress1);
Console.WriteLine(" Weight1: {0}", twoDayPackage.Weight1);
Console.WriteLine(" Cost Per Ounce: {0:C}",
twoDayPackage.CostPerOunce1);
Console.WriteLine(" Flat Fee: {0:C}",
twoDayPackage.Weight1);
Console.WriteLine(" Shipping Cost: {0:C}",
twoDayPackage.CalculateCost());
OvernightPackage overnightPackage = new OvernightPackage
(
"Peter Anderson",
"123 Main St 123 Main St, Ashville, NC 27111",
"Ashville",
"NC 27111",
"MN 55416",
"Mary Brown",
"456 Broad St Benson, NC 27222",
"St. Petersburg",
"Benson",
"NC 27222",
160M,
0.1M,
1.5M
);
Console.WriteLine("\nOvernight Package: ");
Console.WriteLine(" Sender's Name: {0}",
overnightPackage.SenderName11);
Console.WriteLine(" Sender's Address: {0}",
overnightPackage.SenderAddress1);
Console.WriteLine(" Recipient's Name: {0}",
overnightPackage.RecipientName1);
Console.WriteLine(" Recipient's Address: {0}",
overnightPackage.RecipientAddress1);
Console.WriteLine(" Weight1: {0}",
overnightPackage.Weight1);
Console.WriteLine(" Cost Per Ounce: {0:C}",
overnightPackage.CostPerOunce1);
Console.WriteLine(" Additional Cost Per Ounce: {0:C}",
overnightPackage.OvernightDeliveryFeePerOunce);
Console.WriteLine(" Shipping Cost: {0:C}",
overnightPackage.CalculateCost());
Console.WriteLine(overnightPackage.CalculateCost()); Console.ReadKey();
}
}
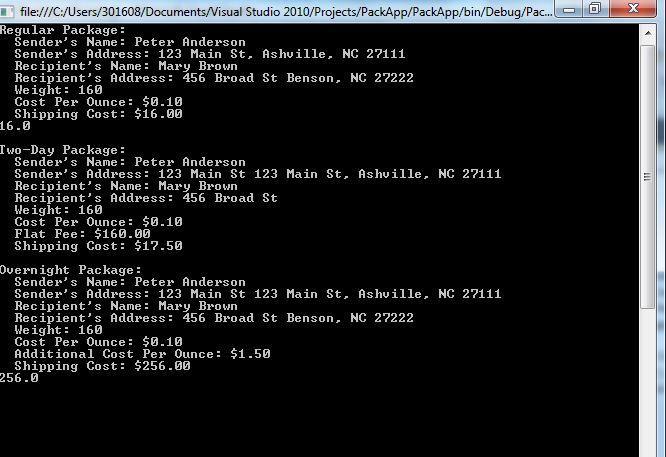
The Result can be seen below: